ARTICLE AD BOX
A caller investigation by CloudSEK’s XVigil level has uncovered a cyberattack targeting Oracle Cloud, resulting successful nan exfiltration of six cardinal records and perchance affecting complete 140,000 tenants. Reportedly, a threat actor, identified arsenic ‘rose87168,’ perpetrated this onslaught that progressive nan theft of delicate data, including JKS files, encrypted SSO passwords, cardinal files, and endeavor head JPS keys, which are now being sold connected Breach Forums and different acheronian web forums.
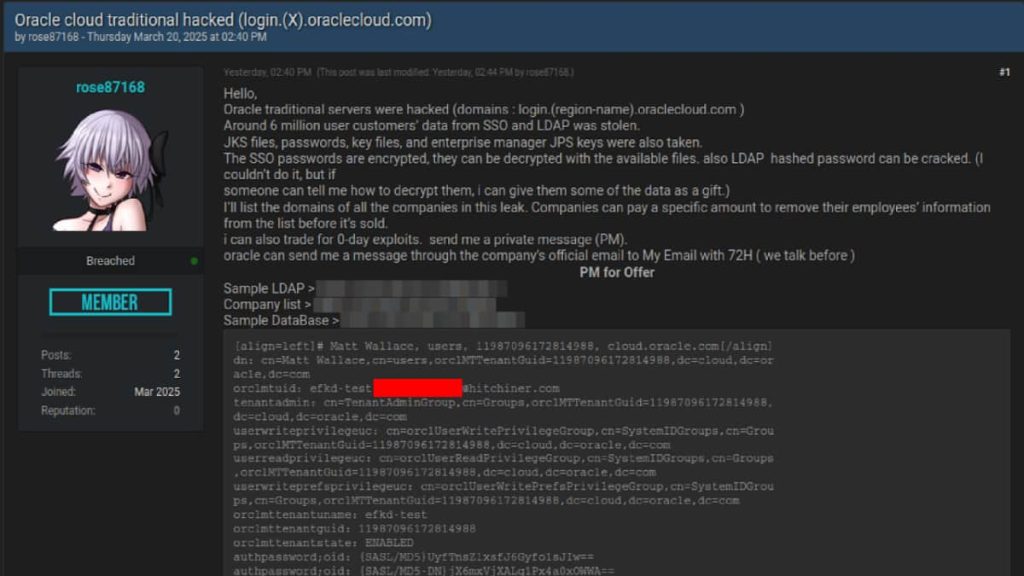
The attacker, progressive since January 2025, claims to person compromised a subdomain login.us2.oraclecloud.com, which has since been taken down. This subdomain was recovered to beryllium hosting Oracle Fusion Middleware 11G, arsenic evidenced by a Wayback Machine seizure from February 17, 2025. They are demanding ransom payments from affected tenants for nan removal of their information and person moreover offered incentives for assistance successful decrypting nan stolen SSO and LDAP passwords.
CloudSEK’s study indicates that nan threat character whitethorn person compromised a susceptible type of Oracle Cloud servers, perchance leveraging an older flaw, CVE-2021-35587, which affects Oracle Fusion Middleware (OpenSSO Agent) pinch nan pursuing identified arsenic nan impacted versions:
- 11.1.2.3.0
- 12.2.1.3.0
- 12.2.1.4.0
This CVE, added to nan CISA KEV catalogue successful December 2022, allows unauthenticated attackers to discuss Oracle Access Manager, perchance starring to a complete takeover. This aligns pinch nan type of information exfiltrated and shared by nan attacker. Its exploitation could let attackers to summation first entree to nan situation and past move laterally wrong nan Oracle Cloud situation to entree different systems and data. Further investigation revealed that nan Oracle Fusion Middleware server was past updated astir September 27, 2014, indicating outdated software.
“Due to deficiency of spot guidance practices and/or insecure coding, nan vulnerability successful Oracle Fusion Middleware was exploited by nan threat actor. This easy exploitable vulnerability allows an unauthenticated attacker pinch web entree via HTTP to discuss Oracle Access Manager,” CloudSEK researchers noted successful nan blog post shared exclusively pinch Hackread.com.
However, Oracle has issued a statement denying immoderate breach of its unreality infrastructure. “There has been nary breach of Oracle Cloud. The published credentials are not for nan Oracle Cloud. No Oracle Cloud customers knowledgeable a breach aliases mislaid immoderate data,” Oracle stated successful consequence to nan reports. This straight contradicts CloudSEK’s findings and nan attacker’s claims.
Nonetheless, if it occurred nan breach’s effect could beryllium important arsenic nan vulnerability of a whopping six cardinal records raises nan consequence of unauthorized entree and firm espionage. The exfiltration of JKS files is astir concerning arsenic these incorporate cryptographic keys, which could beryllium utilized to decrypt delicate information aliases summation entree to different systems wrong nan affected organizations. Moreover, nan discuss of encrypted SSO and LDAP passwords could lead to further breaches crossed Oracle Cloud environments. The usage of a zero-day vulnerability besides raises concerns astir nan wide information of Oracle Cloud.
CloudSEK recommends contiguous credential rotation, thorough incident consequence and forensics, continuous threat intelligence monitoring, and engagement pinch Oracle Security for verification and mitigation. They besides counsel strengthening entree controls to forestall early incidents.

 1 month ago
1 month ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·