ARTICLE AD BOX
Cybersecurity researchers from CYFIRMA person revealed a caller type of Neptune RAT, a distant management instrumentality targeting Windows devices. Marketed connected platforms for illustration GitHub, Telegram, and YouTube pinch claims of being nan “Most Advanced RAT,” nan malware is attracting some newcomers to cybercrime and seasoned hackers looking for a ready-made tool.
What Is Neptune RAT?
Neptune RAT is written successful Visual Basic .NET and is designed to return power of a victim’s Windows computer. Although its creator says nan package is provided for “educational and ethical purposes,” nan tool’s capabilities propose otherwise.
Designed to bargain personification credentials, switch cryptocurrency wallet addresses, and moreover fastener files pinch ransomware features, Neptune RAT gives attackers broad power complete an infected system.
How It Spreads
The malware is distributed freely connected societal platforms. Rather than releasing nan root code, nan developer hides nan executable file, making nan study much complicated. Some of nan malicious codification moreover replaces parts of its strings pinch Arabic characters and emojis, which complicates reversing efforts by researchers. In its free version, Neptune RAT automatically generates PowerShell commands to download and tally further components hosted connected record hosting work specified arsenic catbox.moe.
Dangerous Capabilities
Neptune RAT comes pinch a operation of modules that activity together to discuss Windows computers, including nan following:
- Credential Theft and Clipboard Hijacking: The malware includes a password grabber that extracts login specifications from applications and celebrated web browsers. It besides monitors nan clipboard to observe cryptocurrency wallet addresses, replacing them pinch nan attacker’s own.
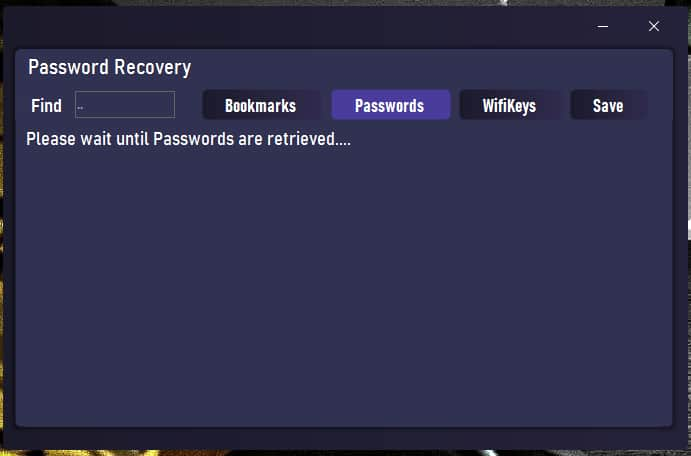 Screenshot from NaptuneRAT’s charismatic website (Credit: Hackread.com)
Screenshot from NaptuneRAT’s charismatic website (Credit: Hackread.com)- Ransomware and System Damage: Once activated, nan RAT tin encrypt files connected nan victim’s computer, extending their extensions to “.ENC, ”and driblet an HTML record pinch ransom information. It whitethorn moreover corrupt strategy components for illustration nan Master Boot Record if an attacker wishes to render nan strategy unusable.
- Evasion and Persistence: To debar being removed, nan malware modifies registry values and adds itself to nan Windows Task Scheduler. It besides checks if it’s moving successful a virtual situation and stops execution if a virtual instrumentality is detected. This operation of techniques helps it support a persistent foothold connected nan system.
- Additional Modules: Separate DLL files adhd further capabilities, including bypassing personification relationship controls, stealing information from various email and browser applications, and moreover enabling unrecorded surface monitoring.
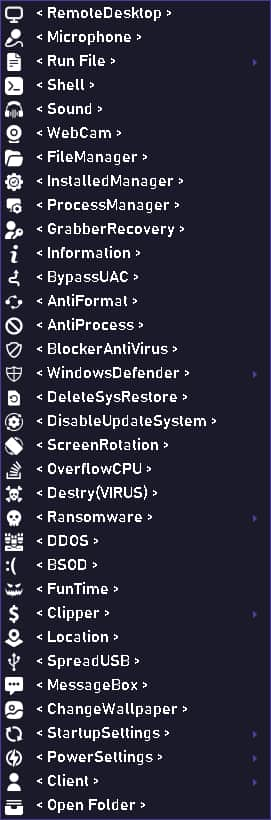 Screenshot from NaptuneRAT’s charismatic website shows nan afloat database of its capabilities (Credit: Hackread.com)
Screenshot from NaptuneRAT’s charismatic website shows nan afloat database of its capabilities (Credit: Hackread.com)Protecting Your System
Since Neptune RAT uses different strategies, some individuals and organizations request to enactment quickly to protect themselves. The champion attack starts pinch immoderate elemental practices: only download package from sources you trust, make judge Windows and each your programs, particularly information tools, are kept up to date, and regularly backmost up immoderate important data.
It’s besides a bully thought to usage anti-virus software that tin support an oculus connected some record changes and web activity, giving you amended protection against thing suspicious.
Expert Insight
Satish Swargam, Principal Security Consultant astatine Black Duck successful Burlington, Massachusetts, offered his position connected Neptune RAT’s evolution. He explained that nan malware uses precocious techniques to extract delicate information from users, spreading done platforms for illustration GitHub, Telegram, and YouTube successful ways that gaffe past modular information tools.
“This instrumentality is particularly concerning because it tin deploy ransomware to fastener your files, starring to awesome interruptions for businesses until nan ransom is paid. It besides lets hackers spy connected screens successful existent clip and moreover switch clipboard contents pinch their ain cryptocurrency wallet addresses,” Swargam noted.
He added that arsenic nan malware continues to adhd caller features, akin to those shared online nether nan banner of acquisition software, organizations request to support changeless monitoring, deploy beardown endpoint defenses, and instrumentality progressive threat discovery measures to trim nan consequence of compromise.

 1 week ago
1 week ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·