ARTICLE AD BOX
A caller phishing run is targeting users crossed Latin America, and astatine nan halfway of it is Grandoreiro, a banking trojan known for stealing delicate financial data. With geofencing and stealthy evasion tactics, this malware is proving difficult to drawback pinch modular defenses.
Let’s return a person look astatine nan campaign, really nan onslaught unfolds, and what makes it truthful effective.
Grandoreiro Attack Overview
Between February 19 and March 14, researchers noticed a surge successful phishing activity tied to Grandoreiro, and signs show nan run is still ongoing.
 A spike of Grandoreiro was detected
A spike of Grandoreiro was detectedGrandoreiro has been astir for years, perpetually evolving to enactment up of detection. It’s designed to bargain banking credentials, show personification activity, and assistance distant entree to attackers.
One of nan standout techniques successful this run is geofencing. Before running, nan malware checks nan victim’s IP reside to find their location. If nan personification isn’t successful a targeted Latin American country, nan malware simply stops executing. This makes nan run much focused, reduces unnecessary exposure, and helps it gaffe past world information monitoring.
Grandoreiro Attack Chain
Grandoreiro is known for slipping past accepted information tools, making it reliable to observe utilizing automated solutions alone. However, pinch nan thief of interactive sandboxes, it’s imaginable to observe nan malware’s afloat behaviour successful existent time.
Here’s a complete look astatine nan execution concatenation wrong a unafraid sandbox:
View sandbox study session
 The afloat execution concatenation of Grandoreiro is displayed wrong ANY.RUN sandbox
The afloat execution concatenation of Grandoreiro is displayed wrong ANY.RUN sandboxUnderstanding nan who, when, and really down this run will thief information teams proactively fortify their defenses. Real-time threat study platforms not only uncover these specifications but besides make them instantly actionable.
Initial Access: Phishing Email
The infection originates pinch a phishing page that lures nan unfortunate into clicking a nexus aliases downloading a clone PDF document. Instead of a PDF, nan record is really a compressed archive (.ZIP aliases .RAR) containing nan Grandoreiro loader.
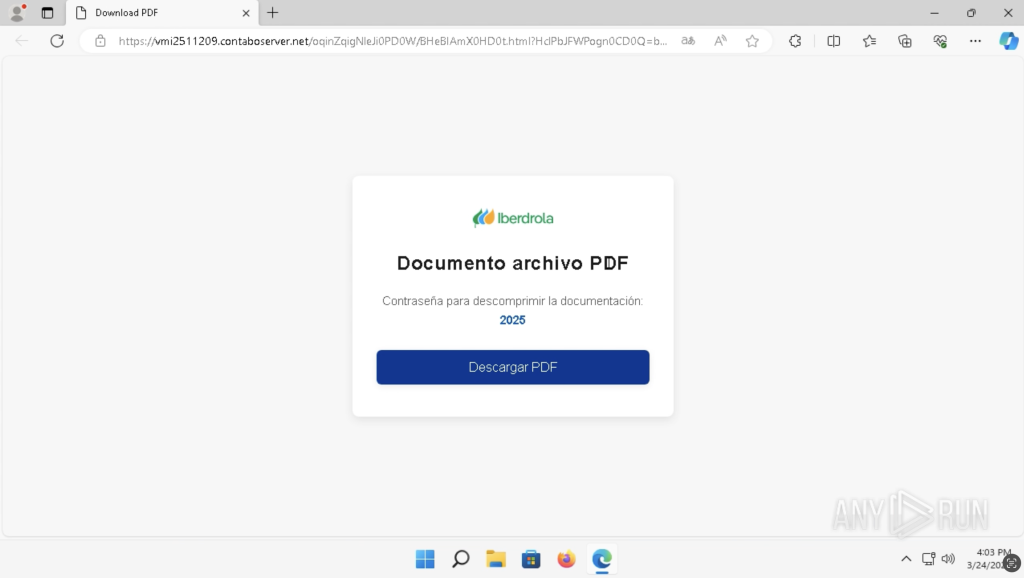 Phishing nexus pinch a clone PDF archive displayed wrong ANY.RUN sandbox
Phishing nexus pinch a clone PDF archive displayed wrong ANY.RUN sandboxExecution & Geofencing
Once nan record is extracted and opened, nan malware sends a petition to ip-apicom to find nan user’s geolocation.
If nan IP reside falls extracurricular nan targeted LATAM countries, nan malware halts execution, but if it matches a targeted region, nan onslaught proceeds.
 Suricata norm triggered wrong ANY.RUN sandbox
Suricata norm triggered wrong ANY.RUN sandboxDNS Evasion: Google DNS
Grandoreiro avoids section DNS queries by sending a petition to dns.google. It provides nan domain sanction of its command-and-control (C2) server, which Google resolves to an IP address.
This measurement helps it bypass DNS-based blocking mechanisms and improves its chances of successful communication.
Traditional solutions often miss these evasion tricks, but ANY.RUN captures them successful existent time, helping teams build effective discovery logic that really reflects really modern malware behaves.
Connection to C2
After resolving nan C2 domain, nan malware sends a GET petition to nan retrieved IP reside to found a connection. This opens nan doorway for nan attacker to present further payloads, bargain credentials, aliases return distant power of nan infected machine.
Grandoreiro successful Action: Tactics & Techniques
Establishing a relationship to nan C2 server is conscionable nan beginning. Once connection is successful, Grandoreiro kicks disconnected a bid of actions designed to enactment hidden, stitchery data, and hole for further exploitation.
In this circumstantial attack, ANY.RUN’s sandbox reveals a wide scope of techniques triggered crossed aggregate MITRE ATT&CK categories. You tin spot each of them mapped successful nan ATT&CK tab of nan study session:
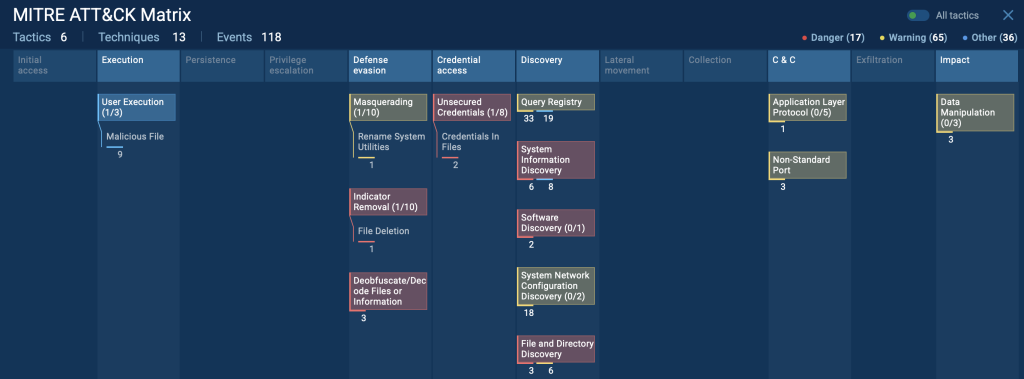 MITRE ATT&CK strategies and techniques utilized by adversaries
MITRE ATT&CK strategies and techniques utilized by adversariesDetection & Response Tips
Detecting Grandoreiro isn’t easy; it blends successful good and uses clever tricks. But here’s really you tin enactment 1 measurement ahead:
- Watch for phishing lures posing arsenic PDF downloads (often .ZIP aliases .RAR archives).
- Monitor outer DNS requests, particularly to dns.google, correct aft execution.
- Flag geolocation lookups to services for illustration ip-apicom; it’s a cardinal portion of Grandoreiro’s filtering tactic.
- Use behavior-based analysis to drawback post-execution strategies for illustration record deletion, credential access, aliases strategy discovery.
Catch nan Attack Before It Spreads
The Grandoreiro run shows really modern threats germinate and why visibility into behaviour matters much than ever.
With ANY.RUN sandbox, information teams tin interact pinch malware successful existent time, uncover hidden tactics, and respond pinch confidence. From phishing to post-exploitation, everything is mapped, visualized, and fresh for action.

 1 month ago
1 month ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·