ARTICLE AD BOX
ESET researchers person mapped nan caller activities of nan CosmicBeetle threat actor, documenting its caller ScRansom ransomware and highlighting connections to different well-established ransomware gangs.
CosmicBeetle actively deploys ScRansom to SMBs successful various parts of nan world. While not being apical notch, nan threat character is capable to discuss absorbing targets.
CosmicBeetle replaced its antecedently deployed ransomware, Scarab, pinch ScRansom, which is continually improved. We person besides observed nan threat character utilizing nan leaked LockBit builder and trying to leech disconnected LockBit’s estimation by impersonating nan infamous ransomware pack some successful ransom notes and leak site.
Besides LockBit, we judge pinch mean assurance that CosmicBeetle is simply a caller connection of RansomHub, a caller ransomware pack progressive since March 2024 pinch quickly expanding activity.
In this blogpost, we analyse CosmicBeetle’s activities during nan past twelvemonth and analyse nan connections to different well-established ransomware gangs. We besides supply penetration into ScRansom.
Key points of nan blogpost:
- CosmicBeetle remains progressive successful 2024, continually improving and distributing its civilization ransomware, ScRansom.
- We supply an study of ScRansom, emphasizing that it is intolerable to reconstruct immoderate encrypted files.
- CosmicBeetle has been experimenting pinch nan leaked LockBit builder and has been trying to maltreatment its brand.
- CosmicBeetle whitethorn beryllium a caller connection of nan ransomware-as-a-service character RansomHub.
- CosmicBeetle exploits years-old vulnerabilities to breach SMBs each complete nan world.
Overview
CosmicBeetle, progressive since astatine slightest 2020, is nan sanction ESET researchers assigned to a threat character discovered successful 2023. This threat character is astir known for nan usage of its civilization postulation of Delphi tools, commonly called Spacecolon, consisting of ScHackTool, ScInstaller, ScService, and ScPatcher. In August 2023, ESET researchers published their insights into CosmicBeetle. Shortly earlier publishing, caller civilization ransomware we named ScRansom appeared that we believe, pinch precocious confidence, is related to CosmicBeetle. We person since recovered further reasons to summation our assurance of this narration and judge that ScRansom is now that group’s ransomware of choice, replacing nan antecedently utilized Scarab ransomware.
At nan clip of that publication successful 2023, we had not observed immoderate activity successful nan wild. That, however, changed soon thereafter. CosmicBeetle has since been spreading ScRansom to SMBs, chiefly successful Europe and Asia.
ScRansom is not very blase ransomware, yet CosmicBeetle has been capable to discuss absorbing targets and origin awesome harm to them. Mostly because CosmicBeetle is an immature character successful nan ransomware world, problems plague nan deployment of ScRansom. Victims affected by ScRansom who determine to salary should beryllium cautious. While nan decryptor itself useful arsenic expected (at nan clip of writing), aggregate decryption keys are often required and immoderate files whitethorn beryllium permanently lost, depending connected really CosmicBeetle proceeded during encryption. We spell into much specifications later successful this blogpost. In keeping pinch our acquisition regarding CosmicBeetle, an absorbing study of immature ransomware groups precocious published by GuidePoint Security shows corresponding results.
CosmicBeetle partially tried to address, aliases alternatively hide, these issues by impersonating nan precocious disrupted LockBit, astir apt nan astir infamous ransomware pack of nan past fewer years. By abusing nan LockBit marque name, CosmicBeetle hoped to amended seduce victims to pay. CosmicBeetle besides utilized nan leaked LockBit Black builder to make its civilization samples pinch a ransom statement successful Turkish.
Recently, we person investigated an absorbing lawsuit that leads america to judge that CosmicBeetle whitethorn beryllium a caller connection of RansomHub. RansomHub is simply a reasonably precocious emerged ransomware-as-a-service pack that quickly gained nan public’s oculus erstwhile Notchy, nan notorious connection of nan BlackCat ransomware pack who claimed work for nan onslaught connected Change Healthcare, complained that BlackCat stole Notchy’s ransom costs and will truthful beryllium partnering pinch nan rival pack RansomHub instead.
This blogpost documents nan improvement of ScRansom for nan past twelvemonth and CosmicBeetle’s attack to compromising victims. We besides dive deeper into nan threat actor’s relations to different ransomware gangs.
Attribution
We judge pinch precocious assurance that ScRansom is nan newest summation to CosmicBeetle’s civilization toolset. In this section, we explicate our reasoning.
ESET telemetry shows respective cases wherever ScRansom deployment overlaps pinch different devices commonly utilized by CosmicBeetle. Additionally, a ZIP archive uploaded to VirusTotal contains 2 embedded archives, each 1 astir apt containing samples from an intrusion. Both archives incorporate ScRansom, ScHackTool, and different devices commonly utilized by CosmicBeetle, further supporting our suspicions.
There is simply a batch of codification similarity betwixt ScRansom and erstwhile CosmicBeetle tooling, namely:
- Delphi arsenic nan programming connection of choice,
- IPWorks room for encryption,
- identical Turkish strings successful nan code,
- using spaces aft colons successful strings, which earned nan Spacecolon toolset its name, and
- GUI similarity pinch ScHackTool.
All of these similarities further fortify our attribution. Although Zaufana Trzencia Strona analysts precocious published a blogpost astir CosmicBeetle wherever they attributed CosmicBeetle to an existent personification – a Turkish package developer, ESET researchers don’t deliberation this attribution is accurate. That attribution is based connected nan civilization encryption strategy utilized successful ScHackTool (not ScRansom). Specifically, they recovered a malicious sample (SHA‑1: 28FD3345D82DA0CDB565A11C648AFF196F03D770) that contains this algorithm and is signed by a Turkish package improvement institution VOVSOFT pinch a strange-looking headquarters.
But nan mentioned sample does not beryllium to VOVSOFT; it is really a malicious patched type of Disk Monitor Gadget, 1 of galore products developed by VOVSOFT signed decently (SHA-1: 2BA12CD5E44839EA67DE8A07734A4E0303E5A3F8). Moreover, nan integer signature was copied from nan morganatic type and simply appended to nan patched version, resulting successful nan malicious sample apparently being signed, but not having a valid signature.
Interestingly, ScHackTool’s encryption strategy is utilized successful nan morganatic Disk Monitor Gadget too. Zaufana Trzencia Strona analysts discovered that nan algorithm apt originates from this Stack Overflow thread from 13 years ago. Since nan writer of nan post, MohsenB, has been an progressive personification of Stack Overflow since 2012 – and, based connected floor plan pictures, is not nan VOVSOFT developer himself – it is apt that this algorithm was adapted by VOVSOFT and, years later, CosmicBeetle stumbled upon it and utilized it for ScHackTool.
Initial entree and victimology
CosmicBeetle often uses brute-force methods to breach its targets. Besides that, nan pursuing vulnerabilities are being exploited by nan threat actor:
- CVE-2017-0144 (aka EternalBlue),
- CVE-2023-27532 (a vulnerability successful a Veeam Backup & Replication component),
- CVE-2021-42278 and CVE-2021-42287 (AD privilege escalation vulnerabilities) done noPac,
- CVE-2022-42475 (a vulnerability successful FortiOS SSL-VPN), and
- CVE-2020-1472 (aka Zerologon).
SMBs from each sorts of verticals each complete nan world are nan astir communal victims of this threat character because that is nan conception astir apt to usage nan affected package and to not person robust spot guidance processes successful place. CosmicBeetle’s leak tract is, arsenic we will show shortly, very unreliable and inconsistent; truthful we mention to ESET telemetry. Figure 1 demonstrates CosmicBeetle’s victims according to ESET telemetry.
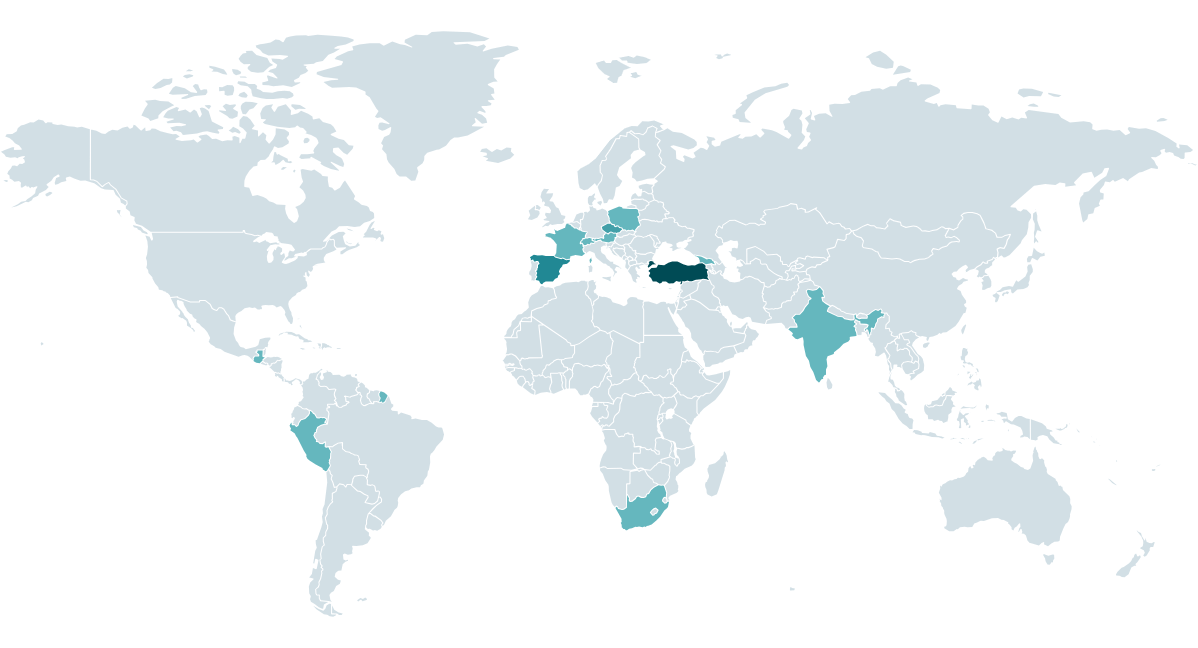 Figure 1. Heatmap of CosmicBeetle attacks since August 2023, according to ESET telemetry
Figure 1. Heatmap of CosmicBeetle attacks since August 2023, according to ESET telemetry
We observed attacks connected SMBs successful nan pursuing verticals:
- manufacturing,
- pharmaceuticals,
- legal,
- education,
- healthcare,
- technology,
- hospitality leisure,
- financial services, and
- regional government.
Brand
Most ransom notes dropped by ScRansom do not delegate a sanction to nan ransomware. CosmicBeetle relies chiefly connected email and qTox, an instant messaging exertion utilized by galore ransomware gangs, chiefly owed to its usage of nan Tox protocol. The Tox protocol provides peer-to-peer end-to-end encrypted communication.
The only sanction CosmicBeetle chose for its civilization ransomware is, ironically, NONAME, arsenic nan threat character concisely branded nan ransomware, which we talk successful nan pursuing section. Due to nan chaotic quality of nan branding, for nan intent of this blogpost, we will proceed to mention to nan ransomware arsenic ScRansom.
LockBit copycat
In September 2023, CosmicBeetle decided to group up a dedicated leak tract (DLS) connected Tor, which it named NONAME. This site, illustrated successful Figure 2, is simply a rip-off of LockBit’s leak tract (see Figure 3).
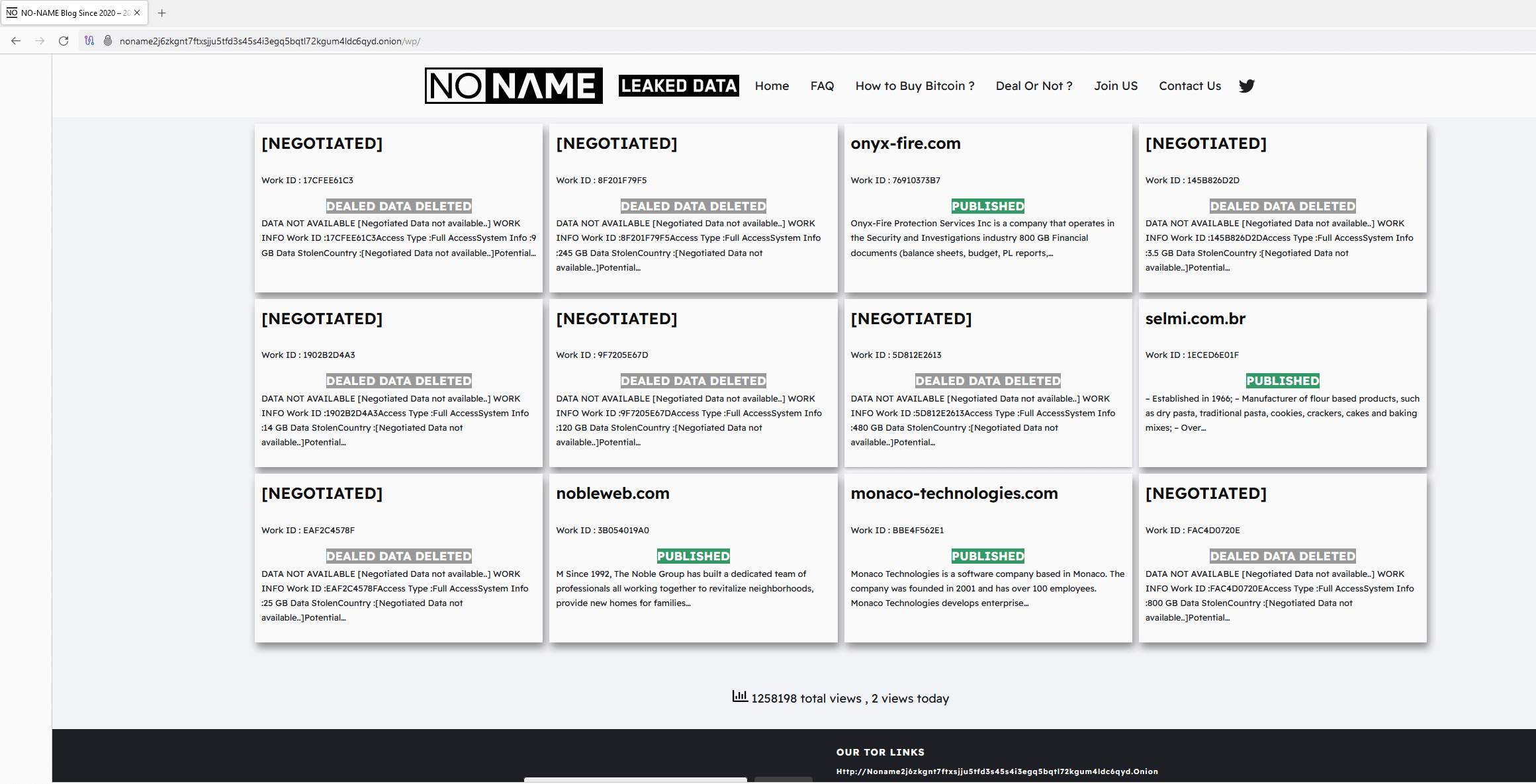 Figure 2. NONAME dedicated leak tract connected Tor
Figure 2. NONAME dedicated leak tract connected Tor
 Figure 3. Typical creation of nan existent LockBit dedicated leak site
Figure 3. Typical creation of nan existent LockBit dedicated leak site
While a fewer graphical changes person been made, nan inspiration is still clear. Moreover, nan creation is not nan only similarity pinch LockBit. All of nan victims visible successful Figure 2 were really compromised by LockBit, not ScRansom. This tin beryllium verified by utilizing DLS search services, specified arsenic RansomLook. All of nan victims were posted connected LockBit’s leak site, astir of them successful September 2023, soon earlier nan NONAME DLS appeared. The Work ID drawstring is added to summation nan illusion of being related to ScRansom, arsenic this is really victims are identified successful ransom notes.
In early November 2023, CosmicBeetle decided to move moreover further and decided to impersonate LockBit completely. They did truthful by registering nan domain lockbitblog[.]info and utilizing nan aforesaid attack arsenic for nan NONAME DLS, only this time, they included nan LockBit logo arsenic good (see Figure 4). Then, for a time, ScRansom’s ransom notes linked to this website. The aforesaid inspiration is visible and nan graphical similarity to nan NONAME DLS (Figure 2) is undeniable.
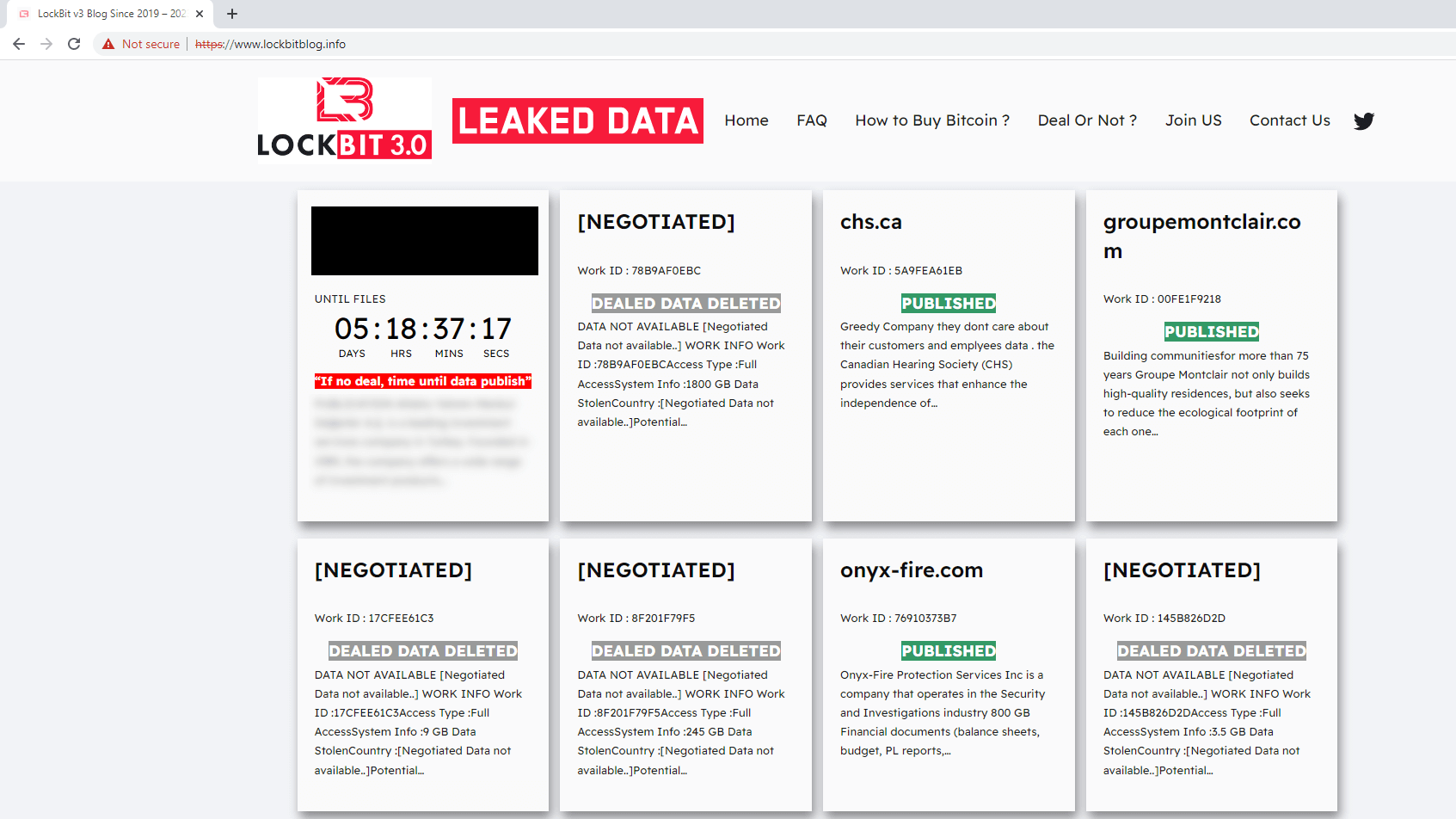 Figure 4. Website mimicking nan charismatic LockBit leak site, group up by CosmicBeetle
Figure 4. Website mimicking nan charismatic LockBit leak site, group up by CosmicBeetle
A sample built utilizing nan leaked LockBit 3.0 builder was uploaded to VirusTotal successful August 2024 from Türkiye. What makes this sample unsocial is that it uses a ransom connection (see Figure 5) successful Turkish and nan qTox ID it mentions is 1 we conclusively linked to CosmicBeetle. ESET telemetry corroborates this connection, arsenic we person investigated a lawsuit wherever deployment of LockBit overlapped pinch CosmicBeetle’s toolset.
I person encrypted your information and for nan interest you will pay, I will reconnect to your system, decrypt it and present it to you.
We would for illustration you to cognize that you cannot get your information backmost pinch known information betterment methods.
These methods will only origin you to suffer time.
However, if you still want to usage information betterment companies aliases programs, please execute and/or person performed nan process connected their copies, not connected your original files.
Corruption of nan original files whitethorn origin irreversible harm to your data.
The originals of your encrypted files person been deleted by utilizing a random information penning technique.
Your backups person been deleted by penning information connected each nan backups successful your NAS Storage and Disks.
If a return is not made wrong 48 hours, nan password utilized successful nan strategy will beryllium deleted and your information will ne'er beryllium returned.
Your disks are encrypted pinch Full disk encryption, unauthorized involution will origin imperishable information loss!
Do not judge nan machine guys who opportunity they will not unfastened moreover if you salary them aliases nan group astir you who opportunity they will return your money and not springiness you your filesI person capable references to spot you
I do not cognize you, truthful location is nary constituent successful having bad feelings towards you aliases doing you harm,my only purpose is to make an income from this business. After your payment,
I will link to your server arsenic soon arsenic imaginable to reconstruct your data.
I will besides explicate really to unafraid your strategy aft this process truthful that specified incidents will ne'er hap to you again.
Personal Key
e-mail 1 : sunucuverikurtarma@gmail[.]com
Backup
e-mail : serverdatakurtarma@mail[.]ru
QTOX : A5F2F6058F70CE5953DC475EE6AF1F97FC6D487ABEBAE76915075E3A53525B1D863102EDD50E
Figure 5. Ransom statement that contains a TOX ID utilized by CosmicBeetle, dropped by a LockBit sample. Text was instrumentality translated from Turkish.
Relation to RansomHub
Using leaked builders is simply a communal believe for immature ransomware gangs. It allows them to maltreatment nan marque of their well-established competitors while besides providing them pinch a ransomware sample that usually useful properly. The LockBit connection, however, is not nan only 1 we person observed.
In June, we investigated an incident involving ScRansom. From our telemetry, we were capable to stitchery nan following:
- On June 3rd, 2024 CosmicBeetle attempted to discuss a manufacturing institution successful India pinch ScRansom.
- After failing, CosmicBeetle tried a assortment of process-killing devices to region EDR protection, namely:
- Reaper,
- Darkside, and
- RealBlindingEDR.
- On June 8th, 2024, RansomHub’s EDR slayer was executed connected nan aforesaid machine.
- On June 10th, 2024, RansomHub was executed connected nan aforesaid machine.
The measurement RansomHub’s EDR slayer was executed is very unusual. It was manually extracted via WinRAR from an archive stored astatine C:\Users\Administrator\Music\1.0.8.zip and executed. Such execution is very different for RansomHub affiliates. On nan different hand, utilizing nan Music files and manually extracting and executing payloads surely is emblematic CosmicBeetle behavior.
To our knowledge, location are nary nationalist leaks of RansomHub codification aliases its builder (though RansomHub itself is astir apt based connected codification bought from Knight, different ransomware gang). Therefore, we judge pinch mean assurance that CosmicBeetle enrolled itself arsenic a caller RansomHub affiliate.
Technical analysis
Similar to nan remainder of CosmicBeetle’s civilization arsenal, ScRansom is written successful Delphi. The earliest samples we were capable to get were compiled astatine nan extremity of March 2023, though, to nan champion of our knowledge, in-the-wild attacks didn’t commencement earlier August. ScRansom is nether ongoing development.
The GUI is emblematic for Delphi applications, though not truthful overmuch for ransomware. All ScRansom samples incorporate a system GUI. The older samples, usually named “Static” by nan developers, require personification relationship to really encrypt anything. While this whitethorn look a complication, it whitethorn beryllium 1 of nan reasons why ScRansom evaded discovery for immoderate time, arsenic moving specified samples successful study sandboxes does not show immoderate malicious activity.
Launching specified an encryptor requires nan threat character to person entree to nan victim’s surface and beryllium capable to manipulate their mouse. This is not nan first clip CosmicBeetle has utilized this attack – ScHackTool is besides a instrumentality that needs to beryllium executed connected nan victim’s instrumentality and requires manual interaction. We are not wholly judge really CosmicBeetle achieves this goal, but guessing from nan different devices used, we judge utilizing VPN entree pinch antecedently stolen credentials and RDP is nan astir probable scenario.
CosmicBeetle besides has experimented pinch a seldom seen version named “SSH”. The encryptor logic is identical to nan different variants, but alternatively of encrypting section files, it encrypts files complete FTP.
Newer builds utilize automation, though only by simulating clicking nan correct buttons from code. These automated builds, named “Auto” by nan developers, are usually bundled wrong an MSI installer together pinch mini devices aliases scripts to delete protector copies. The GUI is hidden by default; its astir caller type is illustrated successful Figure 6.
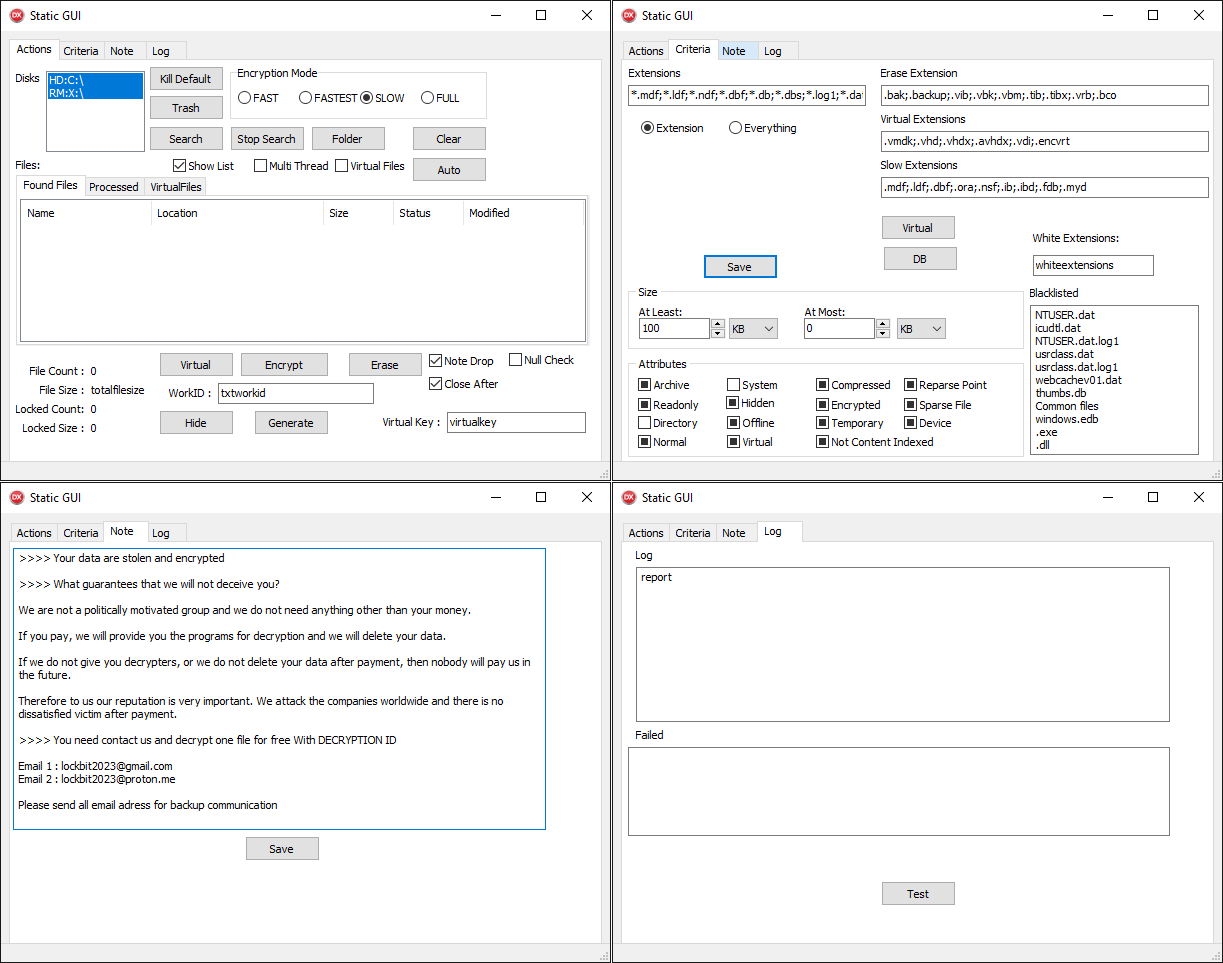 Figure 6. User interface of ScRansom
Figure 6. User interface of ScRansom
A analyzable GUI pinch a batch of buttons, immoderate of which do nothing, is emblematic for CosmicBeetle. While nan GUI pinch 4 tabs looks complex, nan functionality is really very straightforward. ScRansom encrypts files connected each fixed, remote, and removable drives based connected a hardcoded database of extensions (see Appendix A: Targeted record extensions) – this database tin beryllium modified via nan matter container branded Extensions.
ScRansom employs partial encryption – only parts of nan record are encrypted. Five encryption modes are supported:
- FAST
- FASTEST
- SLOW
- FULL
- ERASE
The first 4 modes simply disagree successful really nan ransomware decides what portions of nan record to encrypt. Their utilization seems to still beryllium partially successful development, arsenic not each of nan modes are used. The past mode, ERASE, is important, nevertheless – erstwhile applied, selected portions of targeted files are not encrypted but their contents are replaced pinch a changeless value, rendering these files unrecoverable. Which mode is applied for a fixed record is wished either via nan power buttons successful nan Actions tab aliases via nan inclusion of its hold successful nan Criteria tab. The extensions database branded Virtual Extensions triggers a different encryption usability that, however, is identical to nan regular one. As you astir apt guessed, White Extensions should specify a database of extensions excluded from encryption, though this characteristic is not implemented.
Besides encrypting, ScRansom besides kills various processes and services (see Appendix B: Processes killed and Appendix C: Services killed). Recently, a caller Delphi sample was divided disconnected from ScRansom into a portion that we named ScKill, whose sole intent is to termination processes. ScRansom besides employs debug-like features for illustration loading a database of extensions to encrypt from an ext.txt record and ransom statement contented from a note.txt file.
Encryption
Initial ScRansom samples utilized elemental symmetric encryption utilizing AES-CTR-128. Since December 2023, nan encryption strategy has been updated. The caller strategy is rather (unnecessarily) complex. ScRansom, astatine nan start, generates an AES cardinal we will telephone ProtectionKey, and an RSA-1024 cardinal brace we will telephone RunKeyPair.
Every ScRansom sample utilizing this caller strategy contains a hardcoded nationalist RSA cardinal from a brace we will telephone MasterKeyPair. This nationalist cardinal is encrypted utilizing RSA into what CosmicBeetle calls Decryption ID.
For each file, an AES-CTR-128 cardinal that we will telephone FileKey is generated. Portions of nan record are past encrypted utilizing AES pinch FileKey. When ScRansom finishes encrypting a file, it appends information to its end, specifically:
- The drawstring TIMATOMA (or TIMATOMAFULL if nan full record was encrypted).
- The drawstring TBase64EncodingButton12ClickTESTB64@#$% (TESTB64 successful older builds), encrypted by AES utilizing FileKey.
- The pursuing entries, delimited by $ (a dollar sign):
- Hex-encoded RunKeyPair.Public,
- Decryption ID,
- RunKeyPair.Private, encrypted utilizing AES-CTR-128 pinch ProtectionKey, and
- FileKey, encrypted utilizing RSA pinch RunKeyPair.Public.
- Information astir encrypted blocks commencement and their magnitude (absent if nan afloat record is encrypted).
Finally, Decryption ID is stored into a matter record named DECRYPTION_IDS.TXT and besides written successful nan ransom statement named HOW TO RECOVERY FILES.TXT. Decryption ID is different each clip nan encryptor is executed. On consequent execution(s), nan Decryption IDs are appended to nan DECRYPTION_IDS.TXT file, but not updated successful nan ransom note.
The filename (including extension) is past base64 encoded and nan .Encrypted hold appended. Despite nan complexity of nan full process, we person summarized it successful Figure 7.
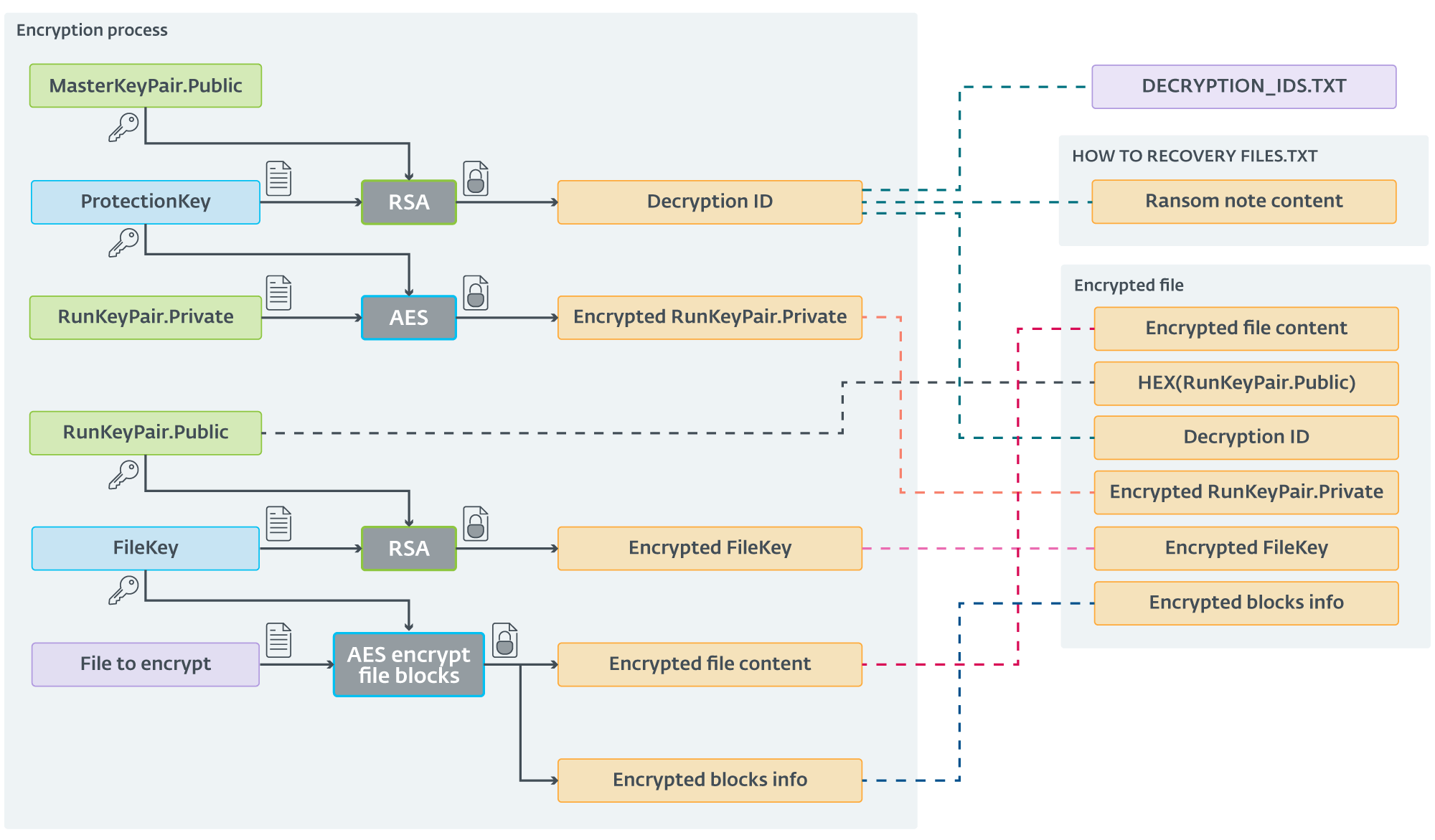 Figure 7. Encryption strategy utilized by nan latest ScRansom samples
Figure 7. Encryption strategy utilized by nan latest ScRansom samples
Decryption
We were capable to get a decryptor implemented by CosmicBeetle for this caller encryption scheme. CosmicBeetle does not supply its victims pinch nan MasterKeyPair.Private cardinal but pinch nan already decrypted ProtectionKey (that needs to beryllium entered successful nan section branded CPriv Aes Key). Additionally, nan decryptor expects nan Decryption ID, which is useless, arsenic nan backstage cardinal is not provided; indeed, nan decryptor ignores its value. The GUI of nan decryptor is illustrated successful Figure 8.
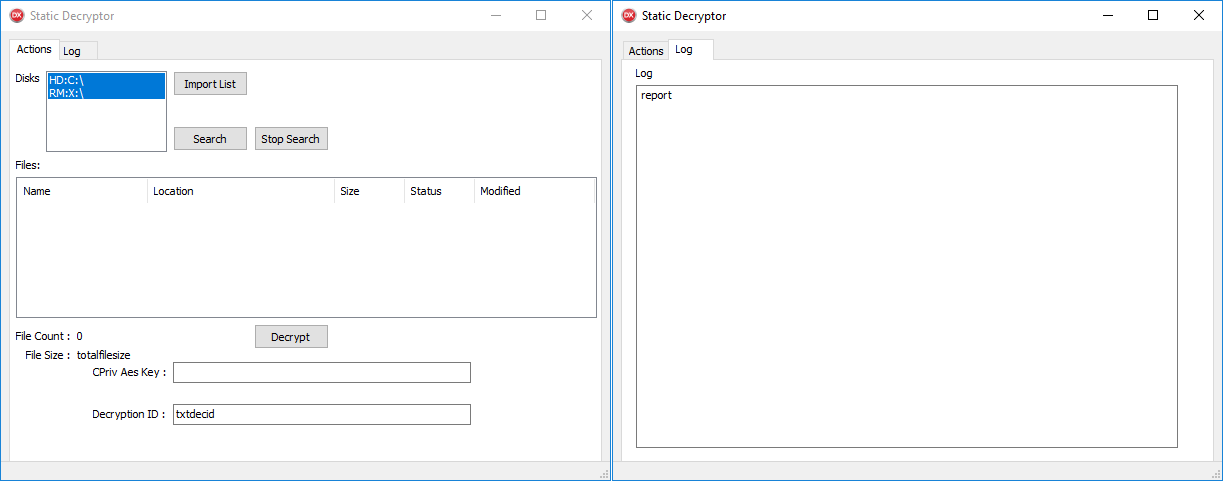 Figure 8. GUI of a ScRansom decryptor. ProtectionKey needs to beryllium entered into nan matter container branded CPriv Aes Key
Figure 8. GUI of a ScRansom decryptor. ProtectionKey needs to beryllium entered into nan matter container branded CPriv Aes Key
If nan correct ProtectionKey is entered, nan decryptor useful arsenic expected. If victims determine to salary nan ransom, they request to cod all Decryption IDs from all nan machines wherever ScRansom was executed. CosmicBeetle past needs to supply a different ProtectionKey for each of nan Decryption IDs. Victims past request to manually tally nan decryptor connected each encrypted machine, participate nan correct ProtectionKey (or effort each of them), click nan Decrypt fastener and hold for nan decryption process to finish.
Moreover, from collaboration pinch 1 of nan victims, we learned that ScRansom was executed much than erstwhile connected immoderate machines, starring to moreover much Decryption IDs. This unfortunate collected 31 different Decryption IDs, requiring 31 ProtectionKeys from CosmicBeetle. Even pinch those, they were incapable to afloat retrieve each of their files. Assuming nan encrypted files were not tampered with, this whitethorn beryllium nan consequence of missing immoderate Decryption IDs, CosmicBeetle not providing each of nan required ProtectionKeys, aliases ScRansom destroying immoderate files permanently by utilizing nan ERASE encryption mode. This decryption attack is emblematic for an immature ransomware threat actor.
Seasoned gangs for illustration to person their decryption process arsenic easy arsenic imaginable to summation nan chances of correct decryption, which boosts their estimation and increases nan likelihood that victims will pay. Typically (like successful nan lawsuit of nan leaked LockBit Black builder), a decryptor is built together pinch an encryptor. When distributed to nan victim, nary further personification effort is required, arsenic nan cardinal is already contained successful nan binary. Additionally, 1 cardinal is capable to decrypt each encrypted files, sloppy of wherever they are successful nan victim’s network.
Conclusion
In this blogpost, we person analyzed CosmicBeetle’s activity complete nan past year. The threat character is still deploying ransomware, though it switched from Scarab to a caller civilization family we telephone ScRansom. Probably owed to nan obstacles that penning civilization ransomware from scratch brings, CosmicBeetle attempted to leech disconnected LockBit’s reputation, perchance to disguise nan issues successful nan underlying ransomware and successful move to summation nan chance that victims will pay.
We besides spotted CosmicBeetle trying to deploy LockBit samples built utilizing nan leaked builder, though only briefly, earlier switching backmost to ScRansom. The threat character puts efforts into continual improvement of ScRansom, changing encryption logic and adding features.
Recently, we observed nan deployment of ScRansom and RansomHub payloads connected nan aforesaid instrumentality only a week apart. This execution of RansomHub was very different compared to emblematic RansomHub cases we person seen successful ESET telemetry. Since location are nary nationalist leaks of RansomHub, this leads america to judge pinch mean assurance that CosmicBeetle whitethorn beryllium a caller connection of RansomHub.
ScRansom undergoes ongoing development, which is ne'er a bully motion successful ransomware. The overcomplexity of nan encryption (and decryption) process is prone to errors, making restoration of each files unsure. Successful decryption relies connected nan decryptor moving decently and connected CosmicBeetle providing all basal keys, and moreover successful that case, immoderate files whitethorn person been destroyed permanently by nan threat actor. Even successful nan best-case scenario, decryption will beryllium agelong and complicated.
For immoderate inquiries astir our investigation published connected WeLiveSecurity, please interaction america astatine threatintel@eset.com.
ESET Research offers backstage APT intelligence reports and information feeds. For immoderate inquiries astir this service, sojourn nan ESET Threat Intelligence page.
IoCs
Files
| SHA-1 | Filename | Detection | Description |
| 4497406D6EE7E2EF561C949AC88BB973BDBD214B | auto.exe | Win32/Filecoder.Spacecolon.A | Auto version of ScRansom. |
| 3C32031696DB109D5FA1A09AF035038BFE1EBE30 | Project1.exe | Win32/Filecoder.Spacecolon.B | Auto version of ScRansom. |
| 26D9F3B92C10E248B7DD7BE2CB59B87A7A011AF7 | New.exe | Win32/Filecoder.Spacecolon.A | Static version of ScRansom. |
| 1CE78474088C14AFB8495F7ABB22C31B397B57C7 | Project1.exe | Win32/Filecoder.Spacecolon.B | Auto encryptor version of ScRansom, Turkish ransom note. |
| 1B635CB0A4549106D8B4CD4EDAFF384B1E4177F6 | Project1.exe | Win32/Filecoder.Spacecolon.A | Static SSH encryptor version of ScRansom. |
| DAE100AFC12F3DE211BFF9607DD53E5E377630C5 | Project1.exe | Win32/Filecoder.Spacecolon.A | Decryptor version of ScRansom (oldest). |
| 705280A2DCC311B75AF1619B4BA29E3622ED53B6 | Rarlab_sib.msi | Win32/Filecoder.Spacecolon.A | MSI record pinch embedded ScRansom, ScKill, BAT book to extremity services, and BAT book to delete protector copies. |
Network
| IP | Domain | Hosting provider | First seen | Details |
| 66.29.141[.]245 | www.lockbitblog[.]info | Namecheap, Inc. | 2023-11-04 | Fake LockBit leak site. |
Ransom statement fragments
Email addresses
- decservice@ukr[.]net
- nonamehack2024@gmail[.]com
- tufhackteam@gmail[.]com
- nonamehack2023@gmail[.]com
- nonamehack2023@tutanota[.]com
- lockbit2023@proton[.]me
- serverrecoveryhelp@gmail[.]com
- recoverydatalife@gmail[.]com
- recoverydatalife@mail[.]ru
Tox IDs
- 91E3BA8FACDA7D4A0738ADE67846CDB58A7E32575531BCA0348EA73F6191882910B72613F8C4
- A5F2F6058F70CE5953DC475EE6AF1F97FC6D487ABEBAE76915075E3A53525B1D863102EDD50E
- F1D0F45DBC3F4CA784D5D0D0DD8ADCD31AB5645BE00293FE6302CD0381F6527AC647A61CB08D
- 0C9B448D9F5FBABE701131153411A1EA28F3701153F59760E01EC303334C35630E62D2CCDCE3
Tor links
- http://nonamef5njcxkghbjequlibwe5d3t3li5tmyqdyarnrsryopvku76wqd[.]onion
- http://noname2j6zkgnt7ftxsjju5tfd3s45s4i3egq5bqtl72kgum4ldc6qyd[.]onion
- http://7tkffbh3qiumpfjfq77plcorjmfohmbj6nwq5je6herbpya6kmgoafid[.]onion
MITRE ATT&CK techniques
This array was built utilizing version 15 of nan MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Reconnaissance | T1595.002 | Active Scanning: Vulnerability Scanning | CosmicBeetle scans its targets for a database of vulnerabilities it tin exploit. |
| T1590.005 | Gather Victim Network Information: IP Addresses | CosmicBeetle scans nan net for IP addresses susceptible to nan vulnerabilities it tin exploit. | |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains | CosmicBeetle registered its ain leak tract domain. |
| T1587.001 | Develop Capabilities: Malware | CosmicBeetle develops its civilization toolset, Spacecolon. | |
| T1588.002 | Obtain Capabilities: Tool | CosmicBeetle utilizes a ample assortment of third-party devices and scripts. | |
| T1588.005 | Obtain Capabilities: Exploits | CosmicBeetle utilizes publically disposable PoCs for known exploits. | |
| T1588.001 | Obtain Capabilities: Malware | CosmicBeetle astir apt obtained ransomware from RansomHub and nan leaked LockBit 3.0 builder. | |
| Initial Access | T1190 | Exploit Public-Facing Application | CosmicBeetle gains first entree by exploiting vulnerabilities successful FortiOS SSL-VPNand different public-facing applications. |
| Execution | T1204 | User Execution | CosmicBeetle relies connected personification execution for immoderate of its tools, though this is usually done by nan threat character via RDP. |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | CosmicBeetle executes various BAT scripts and commands. | |
| T1059.001 | Command and Scripting Interpreter: PowerShell | CosmicBeetle executes various PowerShell scripts and commands. | |
| Persistence | T1136.001 | Create Account: Local Account | CosmicBeetle often creates an attacker-controlled administrator account. |
| Defense Evasion | T1078 | Valid Accounts | CosmicBeetle abuses valid accounts whose credentials it successfully obtains. |
| T1140 | Deobfuscate/Decode Files aliases Information | ScRansom samples protect nationalist RSA keys by encryption. | |
| Credential Access | T1110.001 | Brute Force: Password Guessing | CosmicBeetle utilizes RDP and SMB brute-force attacks. |
| T1212 | Exploitation for Credential Access | CosmicBeetle exploits known vulnerabilities to get credentials. | |
| Impact | T1485 | Data Destruction | CosmicBeetle renders immoderate encrypted files unrecoverable. |
| T1486 | Data Encrypted for Impact | CosmicBeetle encrypts delicate files connected compromised machines. |

Appendix A: Targeted record extensions
This configuration is hardcoded successful each ScRansom sample and is taxable to predominant change. The pursuing sections incorporate nan astir caller configuration astatine nan clip of writing.
Filename masks to encrypt
| *._ms *.0001 *.001 *.002 *.003 *.004 *.005 *.006 *.007 *.008 *.1* *.2* *.3* *.3dm *.3dmbak *.3ds *.4* *.5* *.6* *.7* *.7z *.8* *.9* *.a01 *.a02 *.a03 *.a06 *.accdb *.ACD *.adm *.afi *.ai *.alt *.arc *.arc *.archive *.ard *.asm *.avhdx *.avi *.axf *.b1 *.bac *.backup *.bak *.BBCK *.BBCK3 *.bck *.bco *.bdmp *.bi4 *.bik *.bin *.bkf *.bkp |
*.bkup *.blend *.box *.bpf *.btr *.bup *.c1 *.cbd *.cbu *.cdr *.cdx *.cfgbak *.cgd *.couch *.csv *.ctf *.d0 *.d1 *.d2 *.d3 *.d4 *.da1 *.da2 *.da3 *.da4 *.danger *.dat *.db *.db1 *.db2 *.dbc *.dbdmp *.dbf *.dbs *.dbw *.df *.dft *.diff *.dmp *.doc *.docx *.dwg *.dxf *.dxt5_2d *.ebk *.edb *.edp *.elg *.eml *.encvrt *.fbf *.fbk *.fbw *.fdb *.fmp12 |
*.fp5 *.fp7 *.frm *.ful *.full *.fxl *.gan *.gbk *.gdb *.gho *.ghs *.hbp *.hlp *.hrl *.ib *.ibd *.idx *.imd *.indd *.itdb *.iv2i *.jet *.jpg *.L5X *.lbl *.ldb *.ldf *.llp *.log *.log1 *.lst *.mat *.max *.mdb *.mdbx *.mdf *.mmo *.mov *.mp4 *.mrimg *.msg *.mtx *.myd *.myi *.nb7 *.nbf *.ndf *.ndk *.ndx *.nsf *.nsg *.ntf *.nx1 *.nyf *.obk |
*.oeb *.ol2 *.old *.one *.ora *.ost *.ostx *.ova *.pak *.par *.pbd *.pcb *.pdb *.pod *.ppt *.pptx *.pqb *.pri *.prt *.psd *.psm *.pst *.pstx *.ptb *.qba *.qbb *.qbm *.qbw *.qic *.qrp *.qsm *.qvx *.rar *.raw *.rbf *.rct *.rdb *.redo *.rfs *.rman *.rpd *.rpo *.rpt *.rtf *.sai *.saj *.seq *.sev *.sic *.sko *.skp *.SLDASM *.SLDDRW *.SLDLFP |
*.SLDPRT *.sldprt *.sldrpt *.slp *.sna *.sna *.spf *.spl *.sql *.sqlaudit *.sqlite *.sqlite3 *.srd *.step *.stm *.stp *.tar *.tar.gz *.tga *.tgz *.tib *.tibx *.tif *.tiff *.tmp *.trc *.trn *.tuf *.upd *.usr *.vbk *.vbm *.vct *.vcx *.vhd *.vhdx *.vib *.vix *.vmdk *.vmsd *.vmsn *.vmx *.vmxf *.vob *.vrb *.vswp *.wim *.wt *.xls *.xlsm *.xlsx *.zip *ibdata |

 8 months ago
8 months ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·