ARTICLE AD BOX
Credential theft alert! Venak Security discovers a BYOVD onslaught utilizing .SYS drivers to bypass Windows security. Learn really this onslaught steals personification information and gains control.
A caller investigation by Venak Security uncovered an onslaught script that leverages a vulnerability wrong a kernel-level driver associated pinch Checkpoint’s ZoneAlarm antivirus software. The susceptible driver, vsdatant.sys, type 14.1.32.0, pinch an MD5 hash of 190fe0ce4d43ad8eed97aaa68827e2c6, was nan halfway constituent of nan exploit.
This driver was primitively released successful 2016 and became a constituent of introduction for malicious actors employing a method known arsenic “Bring Your Own Vulnerable Driver” (BYOVD). This method allowed nan attackers to summation elevated privileges wrong nan compromised systems, efficaciously bypassing important Windows information features, including Memory Integrity- a Windows information characteristic that uses virtualization to safeguard nan system’s representation from malicious codification and drivers.
Researchers noted that BYOVD has go a favoured instrumentality among cybercriminal groups seeking to disable Endpoint Detection and Response (EDR) products. For your information, nan BYOVD attack involves introducing susceptible drivers onto targeted systems and exploiting them to execute malicious codification astatine nan kernel level. A cardinal facet of this method is nan maltreatment of digitally signed drivers. Because these drivers transportation valid signatures, they look morganatic to information software, efficaciously bypassing detection.
As per Venak Security’s research, nan onslaught starts pinch a malicious email containing a Dropper, which downloads and executes a book that installs nan susceptible driver (.SYS file) and registers it arsenic a service.
The driver interrupts Core Isolation and removes process protection. The attacker past extracts personification credentials, sends them to a Command and Control Server, and uses Remote Desktop to summation persistent power of nan compromised machine. This image demonstrates really this onslaught was implemented:
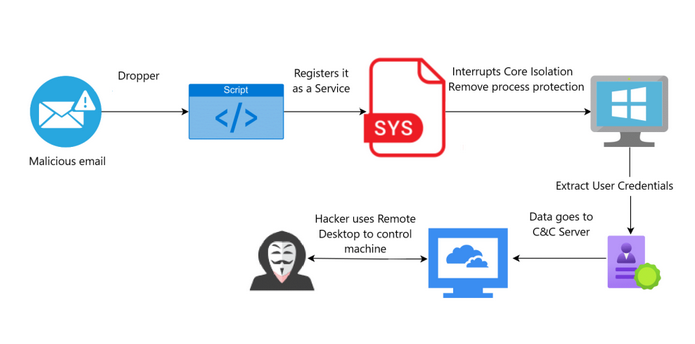 Source: Venak Security
Source: Venak SecurityResearchers noted that while Memory Integrity isolates protected processes wrong a virtualized environment, making it difficult for attackers to inject malicious code, nan susceptible vsdatant.sys driver allowed nan attackers to bypass these protections, rendering nan characteristic ineffective.
Since vsdatant.sys features high-level kernel privileges, nan vulnerability allowed nan attackers to evade modular information protocols and summation complete power complete nan infected machines while remaining undetected. Resultantly, nan attackers could entree and extract delicate information, including personification passwords and stored credentials.
Furthermore, nan susceptible driver carried a valid integer signature, which is nan logic why emblematic EDR solutions grounded to observe nan attack, classifying it arsenic safe. This allowed nan malicious activity to proceed without triggering information alerts. Venak Security was capable to replicate nan onslaught and show its execution. This highlights a captious limitation of accepted information measures against BYOVD attacks.
Check Point reached retired to Hackread.com pinch a connection emphasising that nan susceptible driver mentioned by Venak Security is outdated and not coming successful existent versions of their products, and users pinch updated ZoneAlarm aliases Harmony Endpoint are safe.
“The susceptible driver referenced by Venak Security (vsdatant.sys, type 14.1.32.0) is outdated and nary longer successful usage successful existent versions of our products. Users moving nan latest versions of ZoneAlarm aliases Harmony Endpoint are not affected, arsenic these see updated drivers that reside this issue. After a thorough review, we tin corroborate that versions released successful nan past 8 years are not susceptible to this issue. For afloat protection, we urge users guarantee they are moving nan astir caller type of Check Point ZoneAlarm aliases Check Point Harmony Endpoint, which includes enhanced safeguards against BYOVD-style attacks.”
Check Point’s SpokespersonIt is important to statement that nan astir existent type of nan driver does not incorporate this vulnerability and Checkpoint has been informed of nan issue. Still, nan findings show nan value of driver information and nan request for vendors to inspect their drivers for vulnerabilities thoroughly.

 1 month ago
1 month ago







 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·